Shield ICCP communications from quantum threats with IPsec

Power utilities are increasingly aware of the urgent need to protect their critical grid communications and data from cyber threats and attacks powered by quantum computing. Making Inter-Control Communications Protocol (ICCP)-based data exchanges quantum-safe has emerged as a hot topic and key priority for utilities as they work to deal with these emerging threats and maintain compliance with mandatory cybersecurity standards.
Why the ICCP is important to grid operations
The ICCP, also known as Telecontrol Application Service Element 2 (TASE.2), is defined by the IEC 60870-6 TASE.2 standard. As an integral part of energy management systems (EMSs), it is the de facto worldwide standard for control center communications between utilities and other electric system entities, including transmission system operators (TSOs), independent power producers (IPPs) and balancing authorities (BAs).
These entities use the ICCP to exchange real-time and historical power system telemetry, monitoring and control data, including measured values, data quality codes, scheduling data, energy accounting data and operator messages (Figure 1).
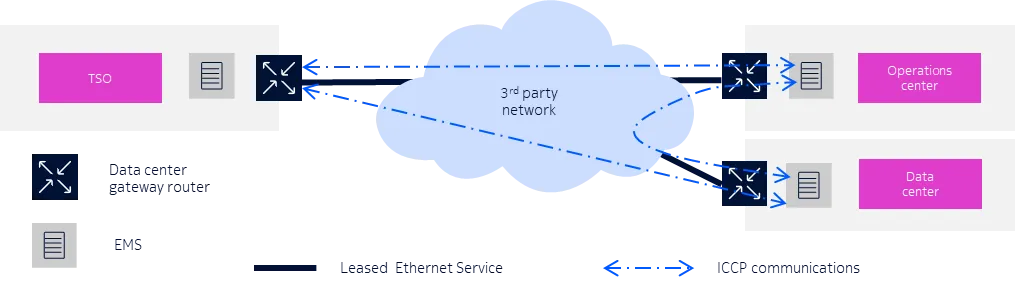
Figure 1: Utilities use ICCP to exchange data with TSOs and other entities
These exchanges play a critical role in today’s increasingly interconnected power grids. They enable utilities to continuously balance generation and transmission capabilities against load demand and exchange critical operational data to keep their grids running in a stable and reliable way. But ICCP is also an unprotected protocol that must be encrypted and authenticated to reduce its vulnerability to integrity violation, interception, alteration, spoofing and eavesdropping.
Why securing ICCP data exchanges is a necessity
Given the vital role that ICCP data exchanges play in the operation of BAs, TSOs and other grid entities, a successful cyberattack on ICCP communications can have severe consequences. For example, compromised ICCP communications lead to loss of visibility between BAs and TSOs, which disrupts coordinated grid operations and causes incorrect or delayed control actions.
In extreme cases, these effects may escalate into widespread blackouts. Given these high-impact risks, it’s no surprise that the power industry’s regulatory authorities require utilities to shield these exchanges from cyber threats.
For example, the North American Electric Reliability Corporation (NERC) mandates that utilities protect the confidentiality, integrity and availability of ICCP communications (see NERC CIP-12-2 A.3). NERC CIP-12-2 B.R1 requires utilities to mitigate the risks of unauthorized disclosure. NERC CIP-12-2 B.M1 states that mitigation methods such as encryption must be used to safeguard against the unauthorized disclosure and modification of data as it is being transmitted between control centers.
Today, most utilities secure ICCP communications using asymmetric public/private key encryption methods such as Diffie–Hellman (DH) and Rivest–Shamir–Adleman (RSA), as specified in IEC 62351-4 Ed. 1.1 (section 5.1). The network that connects the various entities may be supplied by a third-party telecommunication provider, with connectivity offered as either layer 2 or layer 3 services.
This architecture can limit the applicability of Ethernet-based encryption solutions such as MACsec. In light of these constraints, IPsec should evolve to provide the level of reliability required to withstand attacks originating from classical and quantum computing threats.
How quantum computing puts ICCP infrastructure at risk
Quantum computers rely on quantum bits, or qubits, that can simultaneously execute vast numbers of complex mathematical calculations. When practical quantum computers with high-quality qubits become reality, they will change the way industries work and unlock innovation that will help solve the biggest challenges in practically every field.
But bad actors have uses for practical quantum computers, too. In particular, they are eager to gain access to cryptographically relevant quantum computers (CRQCs), the term for quantum computers that can solve the mathematical problems behind the asymmetric public key cryptography algorithms. With CRQCs, they would have a platform for launching damaging cyberattacks on utilities’ critical network infrastructures and communications—including ICCP communications.
This is a clear and present danger to utilities. Why? Because bad actors already have quantum algorithms they can use with CRQCs. For example, Shor’s algorithm can easily crack DH, RSA and other popular asymmetric encryption methods. Grover’s algorithm halves the level of protection provided by symmetric encryption methods such as the Advanced Encryption Standard (AES), which means today's "safe" 128-bit encryption cannot resist a CRQC attack.
To add more urgency to the issue, bad actors aren’t waiting idly for CRQCs to arrive. Some are actively stealing encrypted grid communications, including ICCP messages, using techniques like fiber tapping. If they acquire a CRQC, they will be able to use it to decrypt the communications. This harvest now, decrypt later (HNDL) approach opens the door to disrupting grid operations with man-in-the-middle (MITM) or denial-of service (DoS) attacks.
Utilities shouldn’t wait for CRQCs, either. It’s time to make ICCP communications quantum-safe.
How to make ICCP communications quantum-safe today
The good news is that quantum protection is available today. Power utilities can take advantage of familiar encryption standards and technologies to build a multilayer, defense-in-depth security framework that shields their ICCP communications—and their entire grid operations infrastructure—against current and future quantum threats. There are two practical ways to start making IPsec quantum-safe right now.
Option 1: Mix pre-shared keys with IKEv2 (RFC 8784)
The first approach comes from RFC 8784, which introduces an enhancement to the IKEv2 key exchange process. It allows utilities to mix in a Post-Quantum Pre-shared Key (PPK), which is a long, high-entropy key that’s exchanged out-of-band. This introduces an additional round of key generation following the traditional DH exchange, ensuring that the resulting keys are resistant to Shor’s algorithm.
What’s great about this method is that it’s a transitional solution. Utilities don’t have to wait for full post-quantum cryptography standards to be finalized. They can start hardening their key exchange mechanisms today.
Option 2: Integrate post‑quantum cryptography into IKEv2
The second approach is based on IETF RFC 9370: Multiple Key Exchanges in IKEv2, which defines a mechanism that enables IKEv2 to perform multiple key exchanges during tunnel setup. This approach allows IPsec to combine both classical and quantum-safe algorithms, thereby strengthening security for future-proof communications. The solution is nearly ready, as most of the building blocks have already been finalized.
Recently, NIST standardized the Module-Lattice Key Encapsulation Mechanism (ML-KEM) as a post-quantum cryptographic algorithm. ML-KEM is a quantum-resistant key encapsulation mechanism designed to withstand attacks from quantum computers. It can be used either independently or in conjunction with traditional key exchanges in IKEv2. The goal is to establish hybrid key exchange models that ensure that all key derivation and keys are safe as long as one key exchange algorithm is safe.
These two approaches significantly improve IPsec’s ability to withstand future quantum threats. They ensure that asymmetric key exchange—the backbone of secure tunnel setup—remains viable in a post-quantum world.
It’s important for utilities to understand that IPsec delivers true end‑to‑end encryption across multiple intermediate IP hops. This capability is a key differentiator compared to symmetric key encryption technologies that operate at lower layers of the network, such as MACsec. While MACsec secures traffic on a hop‑by‑hop basis and is also considered a quantum‑safe solution, its implementation over a multipoint leased connection from a telecommunication provider can be challenging because of the nature of the service being offered.
Get quantum-safe now!
The best time for utilities to get quantum-safe is now. By using proven and familiar technologies to build a multilayer, defense-in-depth security framework, power utilities can get protected and ensure that their critical ICCP communications remain safe as quantum threats move from possibility to reality.
To learn about quantum-safe grid security, join us at DISTRIBUTECH® International 2026, which runs from 2–5 February in San Diego. Stop by booth #3541 to talk with our experts and see a demo on quantum-safe networks featuring some of our networking and security products.







