Five security threats to hunt in Radio Access Networks

Modern Radio Access Networks (RAN) are no longer hardware islands; they’re software-defined, virtualized, and deeply interconnected. That agility comes at a cost: a bigger, more complex attack surface that perimeter defenses alone can’t protect.
Recent intrusions exploiting weak implementations of telecom interfaces and misconfigured network controls like those attributed to groups such as Salt Typhoon and Weaver Ant show how attackers are using “living-off-the-land” techniques to stay invisible, bypass defenses, and move deep into the network.
How confident are you that your radio network hasn’t already been breached?
In this blog, you’ll discover five critical anomalies every telecom operator should hunt for, and why AI-powered threat hunting reveals what routine monitoring misses. These insights come from Nokia’s Advanced Cybersecurity Consulting Services, based on real-world engagements with leading telecom operators, where telco-specific security assessments and proactive threat hunting are now recognized as industry best practices.

Figure 1: Observed cyber kill chain in RAN
1. Unauthorized remote access
What it is: Remote Desktop Protocol (RDP) servers in management environments are prime targets for both external attackers and insider threats, often exploited through weak passwords, phishing or authentication flaws.
Why it matters: Unauthorized RDP access can lead to ransomware or full network compromise.
How to hunt: Query Windows Event Logs for failed RDP logons (Event ID 4625) and filter for patterns like repeated failures from one IP or multiple accounts. SIEM dashboards can visualize these spikes. Example: create a query for high-frequency failed logins from a single source IP targeting multiple accounts.
2. Lateral movement across the management network
What it is: Once inside, attackers aim to move sideways, often through the Network Management System (NMS), to reach more valuable targets.
Why it matters: Compromise of the NMS gives attackers control over multiple network elements, enabling large-scale disruption. Groups like Salt Typhoon and Volt Typhoon have used this tactic.
How to hunt: Watch for accounts behaving oddly, such as an NMS account accessing radio nodes in distant regions or making large-scale configuration changes outside normal hours. Correlation rules in SIEM or Extended Detection and Response (XDR) solutions can highlight unusual authentication paths or privilege use across network segments.
3. Privilege escalation on critical elements
What it is: Attackers rarely settle for basic access; they escalate privileges to gain control over critical systems.
Why it matters: Elevated privileges allow attackers to modify configurations, create new accounts, and execute disruptive commands.
How to hunt: Hunt for accounts suddenly gaining admin rights or performing actions outside their normal role, such as creating new users or modifying system configurations. Compare activity against change-control windows and baseline behaviors. Investigate orphaned or unknown processes running on external IT infrastructure used for network access such as jump hosts or terminal servers.
4. Access abuse on radio nodes
What it is: Attackers or insiders may gain access to the RAN sites by compromising the management plane-, then they may attempt brute-forcing weak or default credentials on radio nodes such as gNBs via SSH for instance. If they succeed, they gain a foothold for deeper attacks.
Why it matters: This technique could be used by threat actors or insiders targeting network elements, and it often precedes privilege escalation or lateral movement.
How to hunt: Look for spikes in failed login attempts from single or distributed IPs targeting management interfaces. Use Security Information and Event Management (SIEM) queries to track authentication failures over short time windows and correlate with geolocation anomalies. Example: filter logs for repeated failures on gNB-DU/CU interfaces within a 10-minute window.
5. Rootkits and suspicious binaries in vendor-specific network functions
What it is: Advanced attackers with access to network functions and/or supporting infrastructure hide in plain sight using rootkits that modify system files and kernel modules to stay invisible.
Why it matters: Nokia’s 2025 Threat Intelligence Report highlights that 45% of surveyed telecom security professionals faced threats using custom-built toolkits designed for telecom infrastructure, enabling attackers to maintain stealth for months. These persistence mechanisms often target lawful interception paths and signaling systems, making detection extremely difficult.
How to hunt: Go beyond basic log analysis. Monitor for unexpected changes to system binaries, unknown kernel modules, or unusual API calls. Integrity checks and anomaly detection tools can reveal hooking techniques used by rootkits to intercept system functions. For example, hunt for modifications in kernel-level drivers or unexplained processes tied to critical network components.
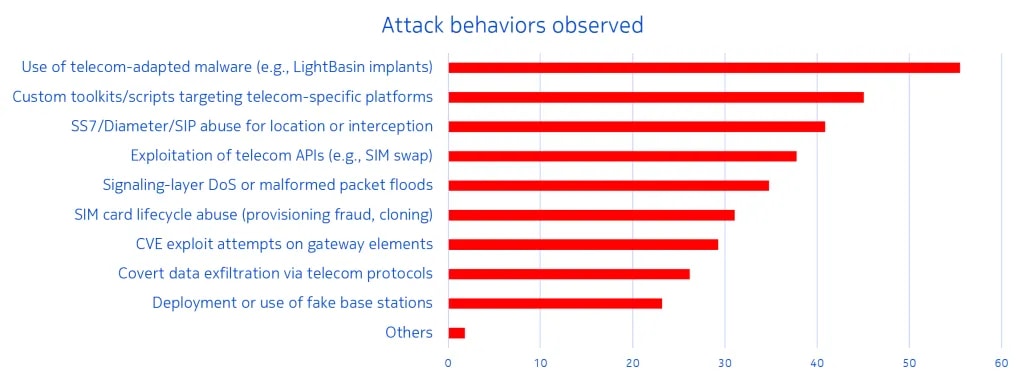
Figure 2: Attack behaviors observed by surveyed telecom security professionals
(source: Nokia Threat Intelligence Report 2025)
Why XDR and AI are critical for RAN threat hunting
Effective threat hunting starts with a clear hypothesis, such as an adversary has gained a foothold in the management network and is now probing for ways to infiltrate the RAN via base stations. From there, the hunt focuses on network traffic and logs originating in the management layer and targeting RAN infrastructure, guided by the latest attack patterns and tactics observed in telecom-specific campaigns.
However, turning a hypothesis into actionable detection requires a multi-layered approach. SIEM platforms remain foundational for aggregating and correlating logs, while SOAR (Security Orchestration, Automation, and Response) accelerates incident response through automation and playbooks. As attacks grow more sophisticated, telecom operators need XDR to unify telemetry across endpoints, networks, and cloud environments, providing the context that SIEM alone cannot.
AI amplifies this stack by detecting subtle patterns, predicting attacker behavior, and reducing false positives at scale. At Nokia, we combine SIEM correlation, SOAR-driven automation, and XDR’s unified detection and response capabilities with AI-powered analytics into a single framework designed for telecom operators. This layered strategy moves beyond reactive monitoring to proactive defense, essential for securing RAN against advanced threats.




