The rise of botnet DDoS

In our just-published Nokia Deepfield Network Intelligence Report: DDoS in 2021, we share the results from one of the largest ongoing studies of real-world Distributed Denial of Service (DDoS) traffic.
Over the last two years, Nokia analyzed more than 10,000 DDoS attacks from internet providers worldwide, including a wide range of regional providers, global transit and cloud companies.
While DDoS is not a new problem (some of us have worked on DDoS for 20 years), the scale and sophistication of recent attacks is different.
Specifically, the Nokia report shows the explosive growth of IoT botnets and an increasingly lucrative extortion market that have fueled exponential growth in DDoS capacity. We now measure IoT botnet and amplifier attack capacity exceeding 10 Tbps -– a significant 3-4x increase from the size of any publicly reported DDoS attacks to date. We further observe aggregate daily DDoS attack volumes peaking over 3 Tb/s during the study period.
In this short series of blog posts here, we will share our perspectives on the technologies and approaches that are available today that equip us with tools to fight DDoS more effectively than ever.
The state of DDoS today
We recently published a report, 'DDoS in 2021', in which we captured our major findings related to DDoS traffic and trends in 2021. By mid-2021, the most damaging DDoS was coming from high-bandwidth, high packet-rate, volumetric DDoS attacks.
For a long time, the basic vendor toolbox to fight DDoS consisted of scrubbing centers (or scrubbers) – dedicated "traffic cleansing" systems to which all traffic is diverted and which then remove traffic identified as malicious and haul the good traffic back to the network.
Scrubber-based countermeasures proved remarkably successful (albeit expensive) against the most common amplification/reflection and synthetic traffic floods. By synthetic here, we mean traffic that is intentionally generated for DDoS attacks (which normally does not exist as such on the internet).
Carriers and cloud providers deployed billions of dollars of dedicated DDoS scrubber appliances and, for a time, gained the upper hand on the attackers.
The times, however, are changing.
The rise of botnet DDoS
The explosive growth in IoT and cloud computing, combined with an increasingly lucrative extortion market, represents a major shift in the DDoS threat landscape.
The days of DDoS launched from compromised home computers with limited bandwidth and running poorly written amateur shell scripts are over. Most DDoS now originates from several hundred sophisticated, commercial booter websites selling a menu of attacks at competitive prices ($50 - $500 US in cryptocurrency). In turn, these booters own or rent cycles on botnets capable of amplification, flood, and application attacks of hundreds of gigabits, millions of packets, or thousands of requests per second.
The torrent of poorly secured IoT devices entering the market each month is fueling the DDoS fire – doubling or tripling the number of exploitable devices each year, with many of them with high-speed Internet connectivity and running full-stack Linux.
Not only are DDoS attacks larger, but they are also significantly more challenging to detect and mitigate. Specifically, most DDoS attacks until now have utilized some form of synthetic traffic generation (e.g., spoofing of their IP addresses) to either reflect/amplify or generate direct traffic floods to target system from a relatively small number of hosting providers which allow IP header modification (IPHM) or compromised home computers.
Scrubbers were effective in mitigating these attacks because synthetic traffic (usually) contained machine learning (ML) distinguishable header or payload features such as poorly randomized headers, patterns in attack payload, or otherwise failed basic scrubber protocol authentication.
In the second half of 2021, in marked contrast to the pre-IoT era, we noticed that most of the largest DDoS attacks exclusively leverage large-scale botnets.
In other words, botnet DDoS dominate DDoS traffic today, from the perspective of overall traffic volumes and daily occurrences - frequency of DDoS attacks. The figure below shows typical daily average peak rates for different types of DDoS attacks. Note that most application DDoS attacks were caused by botnets.
Figure 1. Average peak rates for DDoS attacks per attack type
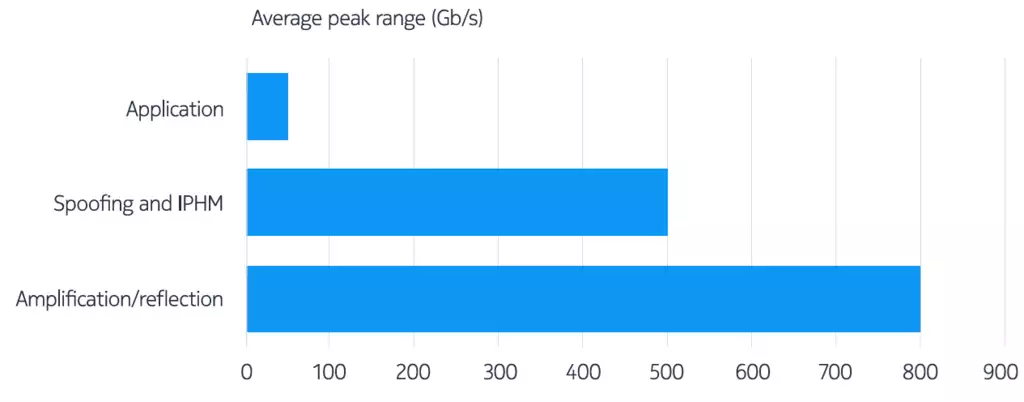
Source: Nokia Deepfield Research, 2H 2021
The trouble with botnet DDoS
Unlike their synthetic amplification/flood predecessors, botnets DDoS traffic uses valid IP addresses, full TCP-IP stacks, legitimate OS-generated protocol headers, correct checksums, and payloads carefully crafted to match the statistical distributions seen in normal application traffic (e.g., web agent, form fields, etc.). Many of the botnets can even pass CAPTCHA challenges.
The challenge for earlier generations of payload-based machine learning scrubber-based solutions is that ML requires meaningful features for extraction (i.e., distinguishable header or payload characteristics). These features are not present in most large-scale botnet DDoS attacks today.
An application botnet DDoS attack with statistically representative HTTP(s) payloads would bypass most ML filters. We recently recorded a botnet DDoS attack which included several million packets from several thousand bot-controlled devices – all with valid TCP/IP headers, statistically representative user-agents, and valid form requests that match those made by legitimate traffic, all aimed at the target website.
In other words, this botnet DDoS attack traffic had no meaningful payload or IP header features to distinguish it from legitimate traffic.
So, given the massive rise in botnets and the increasing ability of botnets to generate realistic application payloads, how can a network operator block the new generation of botnet DDoS?
In the next several blogs, we will outline how advanced technologies like big data analytics and the latest generation of programmable routers, with new ML approaches and better internet security insights, can provide the answer.
The danger of DDoS is real and greater than ever, but we can win over it.
Stay tuned to learn how.
Learn more:
Nokia Deepfield Network Intelligence Report: DDoS in 2021
Nokia Deepfield DDoS Solution
IP Network Security


