Protecting tacit knowledge in the age of agentic AI, through a technology and legal lens

As enterprises accelerate adoption of agentic AI, frontier models and the full AI engineering / AI Ops stack, a new challenge is emerging — one that sits at the intersection of technology, data and law. That challenge is the protection of tacit knowledge.
For decades, organizations recognized people, processes and their data sets as their greatest assets. In today’s AI-driven landscape, that truth is evolving. This tacit knowledge — the invisible know-how, intuition and skill embedded in daily operations — is increasingly being captured, modeled and automated by AI systems. The implications are profound for both productivity and intellectual property (IP) governance.
Tacit knowledge represents the experience-based intelligence that’s difficult to write down but essential to how an organization runs — the way engineers solve a recurring issue, how a support team prioritizes tickets or how operations teams handle complex deployments.
Post-agentic and GenAI era, we must recognize and protect the strategic value of this tacit knowledge. One used to think rightfully that “humans are the most important resources of the company,” but considering the powerful AI engineering tech stack capabilities we have witnessed, we must now recognize that “embedded tacit knowledge in such AI Ops technology” is an equally critical asset.
This blog will explore some communications industry vertical-specific parallels, showing how tacit knowledge protection applies to all enterprises on their journey to agentic AI and AI Ops adoption, especially when the AI Ops is highly closed.
Unlocking tacit knowledge as a critical asset
In the ever-evolving enterprises — industry-specific verticals and our communications sectors are no different — the ability to stay competitive increasingly hinges not only on network infrastructure and market reach, but also on how effectively communications providers can harness tacit knowledge — the often unstructured, experience-based know-how residing in knowledge bases leveraging AI Ops technology.
In industries such as telecommunications, financial services and manufacturing, competitiveness increasingly depends on how effectively organizations can unlock and operationalize tacit knowledge through AI. This knowledge — derived from field experience, network troubleshooting, customer interactions and process optimization — is often unstructured and difficult to codify.
A solution that can best help unlock and harness such knowledge will have the definitive competitive advantage in the agentic AI / AI Ops era.
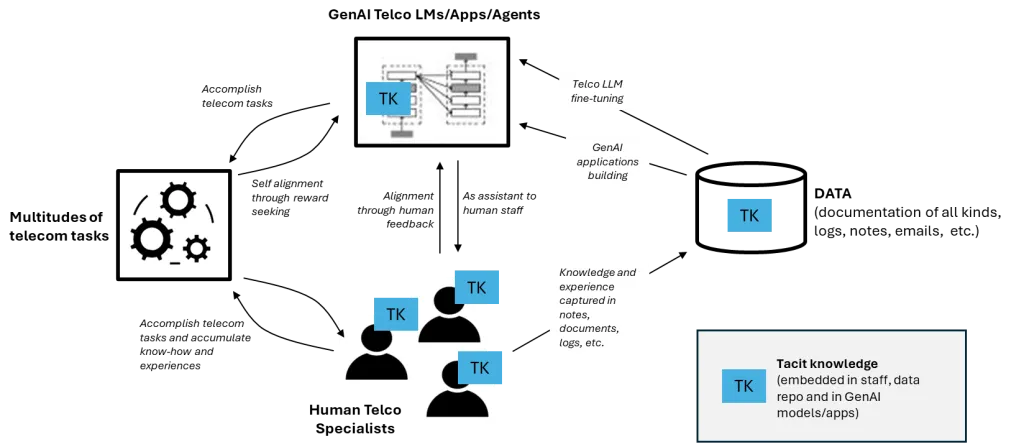
With AI Ops technologies, tacit knowledge becomes the foundation for automation across:
- Network and system design – Learning from historical best practices to guide new deployments.
- Deployment automation – Using AI Ops and GitOps for end-to-end delivery with minimal human intervention.
- Continuous optimization – Applying AI-assisted analytics to improve cost, latency and performance dynamically.
- Customer experience automation – Leveraging prior fault and resolution data to accelerate issue recovery and retention.
AI Ops-based tacit knowledge mining: technology perspective
In recent years, and now more so weekly, we have witnessed an unprecedent pace of innovation in GenAI, agentic AI technology and, correspondingly, its increasing abilities toward automation. Agentic AI and GenAI innovations are accelerating rapidly, but even the most capable models cannot reason over proprietary or vertical-specific knowledge unless it is deliberately infused. True enterprise differentiation will depend on how well companies can extract, structure and embed their tacit knowledge into AI systems.
This is where tacit knowledge infusion comes in. Unlocking tacit knowledge, along with the expertise to pair it with advanced AI engineering techniques, is essential in securing any enterprise structural advantages and our long-term differentiating values. Several key technology areas are called out below:
- Knowledge curation, synthesization, federation and vectorization: Tacit knowledge is often scattered across documents, logs and communications. Curating and cleansing this corpus, then embedding it into vector databases, enables models to access deep organizational context.
- LLM/SLM/RLM-fine tuning: Tacit knowledge infusion into large, small and (more recently) reasoning-centric language models using advanced continuous pre-training (CPT), curriculum training and parameter efficient fine tuning (PEFT) techniques; this enables powerful, open parameter models to acquire deep telco knowledge (with or without RAG assistance).
- Alignment and Reinforcement Learning: Post deployment of agentic AI application, reward-guided fine tuning using various reinforcement learning methods for human objectives is essential to achieve high response quality. This is often referred to as “alignment” and is a form of continuous (self-) learning. Advanced techniques pair human feedback with synthesized data to achieve even better tuning results.
- Agentic workflow: Aiming to act as a “virtual telco specialist,” an AI powered agentic application with tacit telco knowledge can execute complex tasks with a hierarchy of sub-agents and deep agents delivering complex tasks as network traffic optimization, customer care specialist and driving 360-degree customer experiences for networks.
- Multimodal analysis of telco content: In telco and similar sectors, models must interpret network diagrams, call-flow charts and technical schematics. This multimodal comprehension becomes a form of encoded tacit expertise.
With the techniques above, one must recognize that tacit knowledge will be trained into domain-/vertical-specific multi-model farms (the trained model is a carrier of tacit knowledge). To be clear, the models (or similarly vector databases) have now “learned” the tacit knowledge, like how a human employee accumulates skills and expertise over time. In effect, once fine-tuned, models and vector-stores themselves become carriers of tacit knowledge, a form of institutional memory that persists even when employees leave. Protecting these assets becomes as critical as protecting source code or trade secrets.
AI sovereignty and ownership of such AI Ops technology remains a critical control point. Understanding ownership of each sub-component of this complex Industry-specific verticalized AI Ops stack is critical to protecting value leakage.
Protecting tacit knowledge: a legal perspective
With the increasing use of AI Ops for knowledge automation, there are critical intellectual property considerations related to tacit knowledge that must be addressed. First some basic definitions:
Copyright recognizes the value of the way in which an idea, information or knowledge is expressed or displayed, rather than the value of the idea itself. This is one of the most critical forms of IP for enterprise because copyright serves as the legal basis for software licensing, as well as for licensing of proprietary documentation such as user manuals for our equipment.
A trade secret is any business or technical information that is valuable because it is unknown to other parties. The information does not need to cross a certain threshold of inventiveness (like for patents) or originality (like for copyrights) to be eligible for protection. The key is that it must be kept confidential to be entitled to protection.
Risks and control points
Persona-based AI agents (e.g., NetOps Engineer, Security Specialist) fine-tuned on proprietary enterprise data can represent valuable trade secrets or derivative copyrighted works. When customers or vendors use such AI Ops tools, agreements must explicitly define controls points and understand risks around:
- Unauthorized model training or retraining using enterprise data.
- Use of proprietary documentation for embedding or vectorization.
- Redistribution or commercial use of derivative fine-tuned models.
The closed-model dilemma
Enterprises face heightened risk when engaging closed (think open weights, training data sets) AI model vendors that do not guarantee data isolation or non-training clauses. Even if documentation is shared under confidentiality, once that data is used to train a model, control over its internalized knowledge is effectively lost.
Legal recourse — such as breach of contract or IP infringement — is often impractical, as enterprises prioritize customer relationships over litigation. The pragmatic solution is therefore preventive governance, including:
- Metadata tagging of confidential content during knowledge curation.
- Restrictive license terms for AI-related data use.
- Internal AI Ops governance frameworks defining what can or cannot be used for model training.
Protecting tacit knowledge requires both contractual discipline and technical design choices that ensure enterprise data sovereignty.
Strategic implications for enterprises
Tacit knowledge, once invisible and human-bound, is now a digital asset codified in models, embeddings and process data. As enterprises scale agentic AI adoption, they must view their tacit knowledge repositories as both a:
- Strategic differentiator enabling automation and value creation.
- Sensitive intellectual property asset vulnerable to leakage through AI integrations.
Enterprises should therefore:
- Map tacit knowledge flows within AI Ops pipelines.
- Define governance and data ownership policies for AI training and deployment.
- Engage legal, technical and compliance teams to jointly design protective clauses and safeguards.
- Prioritize open or sovereign AI architectures, where feasible, to retain control of embedded enterprise intelligence.
Concluding thoughts
In the era of agentic AI and AI Operations, tacit knowledge is no longer confined to people — it lives in data, processes and models. Harnessing it unlocks automation and innovation. Failing to protect it risks irreversible knowledge leakage and competitive erosion.
Enterprises that combine AI engineering excellence with robust legal governance will define the next generation of intelligent, sovereign organizations — where tacit knowledge is not only leveraged but secured as a core strategic asset.
