XDR Security
Cloud-native Extended Detection and Response
Nokia XDR Security offers a unified and automated approach to threat detection and response, empowering your security teams with actionable intelligence across security layers, automated response mechanisms and a centralized view of the security landscape.
By continuously collecting and correlating security data from endpoints, networks, and cloud environments, Nokia XDR solution provides deep visibility into potential threats. This helps your security teams to quickly investigate, prioritize, and neutralize risks, ensuring a faster, more efficient response to emerging cyber threats. With its intelligent automation, Nokia XDR elevates your security operations and streamlines incident response across your entire infrastructure.
What is XDR?
Extended Detection and Response (XDR) is an advanced security framework that integrates multiple security tools and data sources to provide holistic threat detection and response across an entire network. By combining real-time threat intelligence, network-based sensors, and cognitive threat detection, XDR enables your security teams to detect, investigate, and stop threats such as malware, DDoS activity, and command-and-control traffic before they escalate into breaches.
XDR’s capabilities include advanced analytics that process large volumes of security data, correlating events, and identifying Indicators of Compromise (IOCs). It helps your security teams to quickly triage threats, prioritize incidents, and apply effective countermeasures, such as patch management for vulnerable systems.
Key to XDR’s value is its automation and orchestration features, which integrate multiple security tools into a cohesive system, enabling security experts to execute automated playbooks for threat containment and remediation. These playbooks ensure consistent enforcement of security policies while reducing the manual workload on security teams. By seamlessly integrating with existing security tools, XDR enhances overall security operations and improves response times to evolving cyber threats.
How Nokia XDR Security adds value
Nokia XDR Security enhances your existing security infrastructures by delivering integrated XDR capabilities that work seamlessly with your current security tools. It provides a single pane-of-glass management console, offering your security teams a comprehensive view of your 5G network, including endpoints and cloud environments.
Leveraging advanced analytics, Nokia XDR enables rapid identification, investigation, and management of security incidents, allowing you to prioritize threats effectively. It also coordinates emergency response capabilities for immediate containment, remediation, and repair, all while aligning with security policies.
By unifying and automating processes across security layers, Nokia empowers you to streamline operations, improve response times, and focus on high-priority threats in an evolving cyber landscape.
Claro & Nokia: Securing Colombia’s largest 5G network
Watch the full video to see why Claro chose Nokia as its cybersecurity partner, and how our partnership supports Claro Colombia’s journey towards autonomous networks.
What’s covered:
- The challenges of securing a nationwide 5G network
- How Nokia helps protect critical industries like energy and transport
- The importance of security for autonomous networks
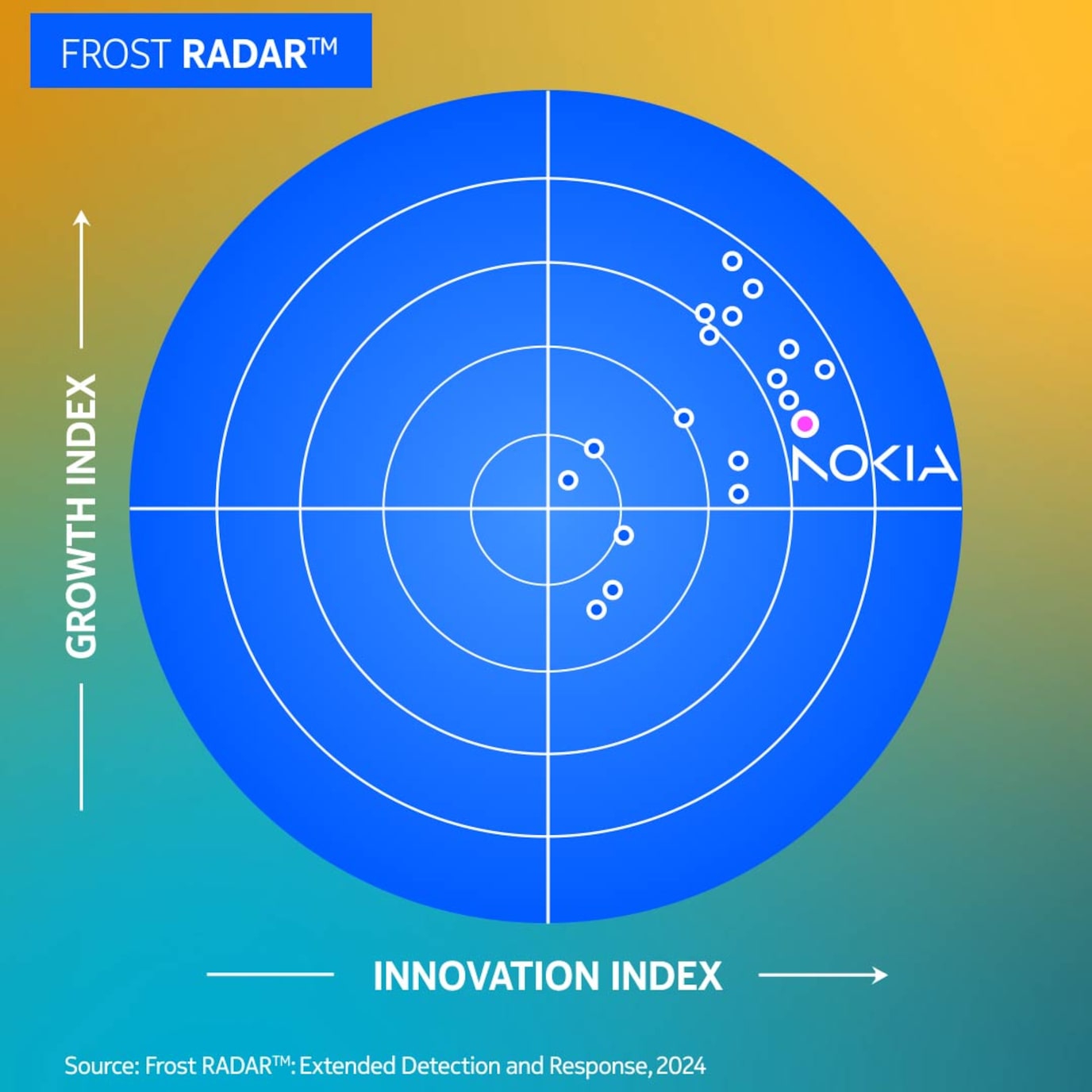
Nokia is telecoms’ XDR choice
Nokia’s recognition in Frost & Sullivan’s Radar Report as #2 innovation leader in XDR reflects our commitment to continuously increase the cyber resilience of critical network infrastructures. Our XDR solution delivers deep visibility and observability across RAN, transport, and core domains.
“Nokia has a unique position in the market as the vendor of choice for telecommunications enterprises, thanks to its comprehensive coverage of telco and OT environments, strong know-how of the industry, connections to the market, and technology capabilities” – notes Lucas Ferreyra in the radar report.
Nokia XDR integrates proactive tools like AI-driven threat hunting, real-time threat intelligence and tailored 5G security use cases and playbooks to help operators secure their networks today while preparing for tomorrow.

Exploring the Evolution of XDR in 5G Networks
As cybersecurity technologies evolve, XDR is becoming essential for addressing the growing threat landscape. The rollout of 5G architecture is driving innovation in telecommunications, requiring a reassessment of security deployment strategies, including XDR.
This white paper examines the integration of XDR within 5G networks, covering:
- Benefits of XDR: How XDR improves threat detection and response across different environments.
- 5G Requirements: The specific security needs and challenges presented by 5G.
- Enhancing 5G XDR with LLMs: Utilizing large language models to boost threat analysis and response.
- Strengthening 5G Security with Nokia XDR: How Nokia’s XDR solutions enhance security in 5G networks.
Click to see what customers and industry analysts have to say
Benefits of XDR

Alert prioritization and classification
Nokia XDR Security integrates alert prioritization and classification capabilities that empower your security teams to swiftly distinguish between false positives and legitimate threats. By automatically identifying and categorizing alerts based on type and severity, XDR eliminates the need for exhaustive investigations into low-priority notifications. This streamlined approach allows security analysts to focus their efforts on countering genuine attacks, thereby enhancing overall security across the network. Additionally, this capability supports you in meeting slice-specific service-level agreements (SLAs), which are essential for enterprise use cases such as smart cities and utilities.

Faster response times
With Nokia XDR Security, you can experience accelerated response times, enabling you to minimize costs and disruptions during attacks or breaches. The unified XDR platform provides visibility from endpoints to the cloud, allowing your security teams to quickly pinpoint the source of potential breaches and reduce threat dwell time. Automated security playbooks continuously augment response actions for various threats, including DDoS attacks and insider threats. This capability not only alleviates the workload on security personnel but also ensures a more effective and efficient response to incidents.

Total visibility across the network
Nokia XDR Security provides comprehensive security by integrating multiple security tools into a coherent and consistent management platform. This unified approach encompasses critical network function protection, audit compliance, privileged access management, certificate lifecycle management, all within a single interface. With a library of connectors for seamless integration with your infrastructure and multi-vendor security tools, XDR correlates data across various sources to create an end-to-end security infrastructure that is easy to manage. This total visibility empowers you to maintain robust security across their networks while effectively addressing evolving cyber threats.

Threat Intelligence Report 2024
Frequently asked questions
XDR enhances security for 5G networks by providing real-time visibility and threat detection across all layers of the network, from endpoints to cloud services. Its ability to correlate data from diverse sources allows for quicker identification of anomalies and potential threats. With 5G networks facilitating increased connectivity and more devices, XDR’s comprehensive approach helps manage the complex threat landscape, ensuring timely responses to prevent breaches.
Key benefits of XDR solutions include:
Holistic threat detection: By integrating data from various security tools, XDR provides a complete view of potential threats, improving detection accuracy.
Automated response: XDR solutions utilize automation to respond to threats more quickly, reducing the workload on security teams and minimizing response times.
Enhanced visibility: XDR offers total visibility across all security layers, allowing organizations to manage security more effectively.
Improved scalability: XDR supports the scalability of security operations, which is crucial for expanding networks like 5G.
Nokia XDR integrates seamlessly with existing security tools by utilizing a unified platform that consolidates data from disparate security solutions. It offers connectors and interfaces to link with various systems, enabling security teams to manage alerts, incidents, and compliance in a coherent manner. This integration helps leverage current security investments while enhancing overall security operations.
XDR reduces latency in security operations by automating threat detection and response processes, which speeds up the analysis and remediation of security incidents. By correlating data in real-time from multiple sources, XDR enables telecom providers to respond to threats faster, minimizing delays that could lead to compromised security. This efficiency is crucial in the fast-paced environment of 5G networks.
XDR supports the scalability of 5G networks by providing a flexible security framework that can adapt to increasing numbers of connected network functions and services. As telecom providers expand their infrastructure to accommodate more users and services, XDR’s ability to integrate and analyze data across various security layers ensures that security measures keep pace with growth, maintaining network integrity without significant manual intervention.
In a telecommunications context, Endpoint Detection and Response (EDR) focuses on protecting critical network functions. EDR provides detailed monitoring and rapid response capabilities to threats on the network function level.
On the other hand, Extended Detection and Response (XDR) offers a broader security solution by integrating and correlating data from multiple sources, including network functions or endpoints, privileged access management tools, network management systems and more. This unified approach enables telecom security teams to identify and address threats that may affect the entire network, particularly in complex environments like 5G.
The NetGuard XDR Security Operations suite comprises:
Product
5G cybersecurity orchestration and incident response software suite to detect, analyze, and mitigate telco security risks faster.
Product
Designed for mission critical infrastructures.
Product
Secure physical or virtual networks with Privileged Access Management (PAM)
Learn more about security operations

Blog

Blog

Article

Article
Blog

Article

Topic

Blog
Latest news
Ready to talk?
Please complete the form below.
The form is loading, please wait...
Thank you. We have received your inquiry. Please continue browsing.

