Today’s challenge
Collaboration ecosystems present an immense opportunity to create novel solutions for automation in industrial, telecom and enterprise contexts. These ecosystems allow entities to share with partners various assets, such as datasets, models and software, to monetize such assets within various marketplaces and to utilize such assets in their products. For example, companies may utilize models and software from vendors to deploy them within their own products or utilize datasets from their customers to develop new products or enhance existing ones.
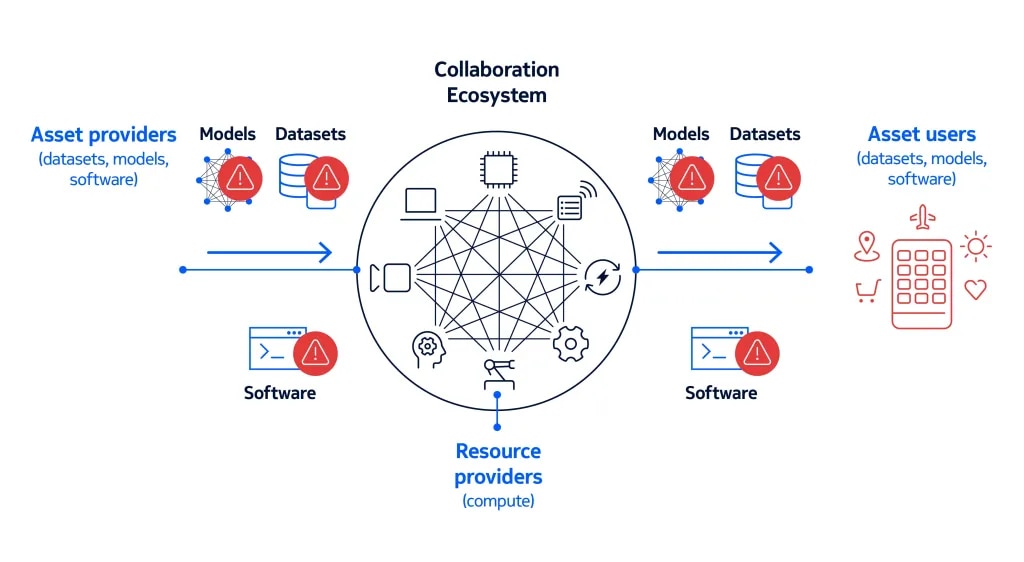
However, the lack of trust between these entities poses a significant barrier to collaboration due to the confidentiality requirements of many assets. Furthermore, increased regulations about AI/ML security and privacy introduce compliance related risks. Although some solutions that rely on manual and costly contractual agreements exist today, addressing the trust requirements between entities in an automated, cost-effective and scalable way presents a challenge.
Our solution
Starting a collaboration between entities usually requires checking whether the assets obtained from collaborators satisfy an entity’s expectations and use case requirements. For example, financial technology startups developing new fraud detection techniques need to ensure that the banks they collaborate with supply transaction data with certain conditions in a certain format. Similarly, pharmaceutical companies developing new drugs need to ensure that the hospitals they collaborate with supply patient data satisfying certain conditions.
In certain industries, checking compliance requirements of regulatory and legal frameworks involves similar actions. These checks usually cover various properties of the assets in question. Examples of such properties and transformations include
- ML datasets having appropriate statistical properties, relevant features and satisfactory measures taken for privacy,
- ML models possessing satisfactory performance and matching lineage for used training datasets,
- Build environments for software binaries whose source-code may not always be available, or reproduction is resource-heavy and time-consuming.
The challenges of trust between entities when exchanging information about the properties of their assets today are usually addressed through contractual agreements among collaboration partners and manual audits by trusted third parties. Creating these contracts and performing these audits are manual, costly, and time-consuming. Efforts in improving automation and security while sharing software and ML models, such as Software Bill of Materials (SBoMs) and Machine Learning Bill of Materials (MLBoMs), usually focus on increasing accountability by creating a provenance trail of the assets being used.
In our Scalable Certification of Confidential Assets solution, we address trust challenges by providing verifiable evidence about the properties and transformations of assets while protecting their confidentiality. This evidence is third-party verifiable, meaning that third party entities can check its correctness. The entities can include not only the recipients or users of the assets in a collaboration but also auditors and regulators. The verifiable evidence is also self-contained, so that no additional infrastructure is needed than what already exists today. As a result, our solution improves compliance with company policies as well as privacy and security requirements of regulatory and legal frameworks.
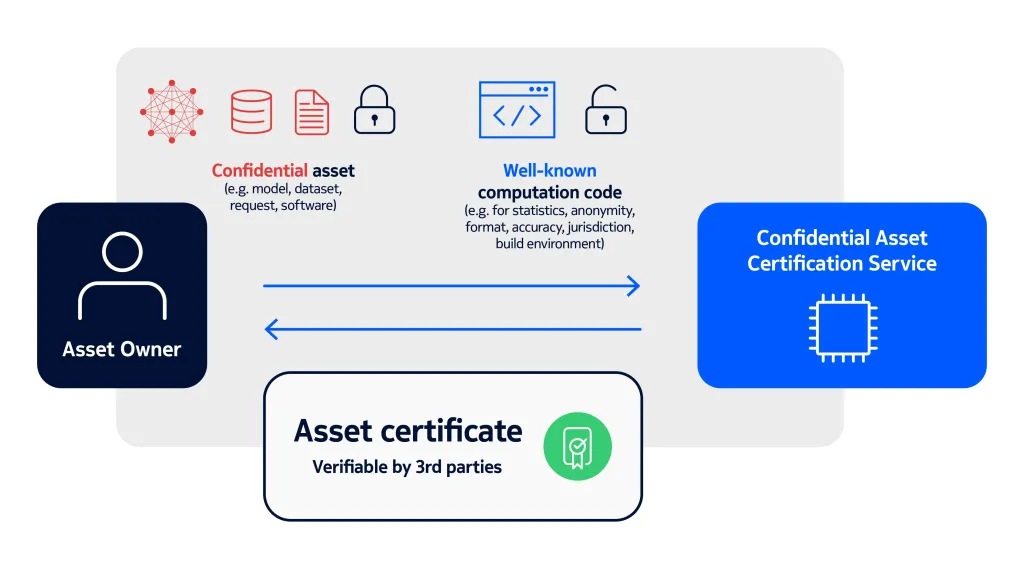
Our Scalable Certification of Confidential Assets solution leverages Trusted Execution Environments (TEEs), readily available in major Cloud Service Providers. Our solution creates third-party verifiable evidence about the properties of different types of confidential assets (e.g., datasets, models, software) in a manner that is cost-effective, automated and secure.
As a result, we enable the creation of trustworthy collaboration ecosystems, improving compliance and security in marketplaces and software supply chains, without sacrificing confidentiality.
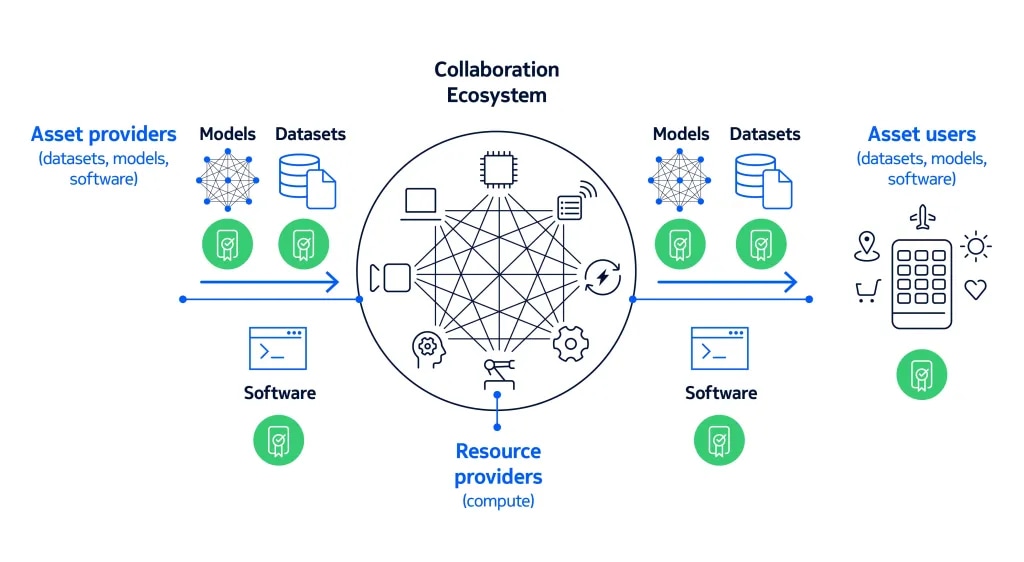
Key technology enablers
Confidential computing
An emerging computation paradigm that protects the confidentiality and integrity of data. Our solution relies on specialized, but commonly available hardware that provides a Trust Execution Environment (TEE). Examples include Intel SGX or TDX, ARM TrustZone and AMD SEV-SNP.
Cloud computing
Provides a cost-effective and scalable solution for outsourcing computation and storage through virtualization that shares underlying physical resources. Increased availability of TEEs in clouds significantly enhances the security for users, allowing them to take advantage of cloud services without having to trust the cloud provider with confidential data and code.
Open-source software
Allows transparency of computations for obtaining the relevant properties of confidential assets. This community can share expertise on improving functionality and security, further enhancing the confidence of users relying on the evidence produced.
Project members
Publications
- duet: Combining a Trustworthy Controller with a Confidential Computing Environment. Istemi Ekin Akkus, Ivica Rimac. Proceedings of the IEEE Workshop on System Software for Trusted Execution (SysTEX), SysTEX 2024, Vienna, Austria, July 2024.
- PraaS: Verifiable Proofs of Property as-a-Service with Intel SGX. Istemi Ekin Akkus, Ivica Rimac, Ruichuan Chen. Proceedings of the IEEE Workshop on System Software for Trusted Execution (SysTEX), SysTEX 2024, Vienna, Austria, July 2024.
- duet code: https://github.com/Nokia-Bell-Labs/tee-duet
- PraaS code: https://github.com/Nokia-Bell-Labs/praas
Please complete the form below.
The form is loading, please wait...
Thank you. We have received your inquiry. Please continue browsing.