From minutes to seconds: Reducing the time to detect DDoS with Sampled Port Mirroring

In the ever-evolving cybersecurity landscape, the tools and techniques we rely on to protect our networks must adapt to address growing and changing threats. For decades, using the NetFlow protocol (along with IPFIX, its standardized evolution) has been a staple in network monitoring and security, offering a method to collect and analyze IP traffic information. But as distributed denial of service (DDoS) attacks become more sophisticated and frequent, we are starting to see some of its limitations.
NetFlow has been widely adopted for its ability to provide detailed visibility into network traffic. It captures metadata such as source and destination IP addresses, ports and protocols, all of which are invaluable for network analytics, performance monitoring and capacity planning.
The vast majority of DDoS detection solutions in service provider networks today use the NetFlow protocol. Our team at Nokia is intimately familiar with NetFlow because we have been relying on it for over two decades – ever since Deepfield’s inception! That said, we have encountered a number of limitations in using NetFlow for DDoS detection:
- Metadata vs. packet capture: NetFlow captures metadata on traffic flows rather than capturing packet content. This metadata is useful for general traffic analysis but it lacks some of the features required for detailed security investigations. For example, flow records can include multiple Transmission Control Protocol (TCP) flags in a combined entry, as opposed to the individual flags in any given packet. NetFlow and IPFIX also don’t report on many of the protocol-specific attributes that can be useful for detecting––and, therefore, mitigating––DDoS more accurately.
- Latency and processing delays: NetFlow records are typically exported at intervals, which can introduce additional latency in threat detection. In the fast-paced environment of a DDoS attack, even small delays can be significant. For example, “losing” 30 to 60 seconds during a DDoS attack often means missing most of the attack traffic because most today’s DDoS events last minutes rather than hours. Immediate detection and response are critical for reducing the impact of an attack, and the inherent delays in NetFlow processing can hinder mitigation efforts.
Last year, we began addressing these limitations by introducing a new method called Sampled Port Mirroring (SPM) into Deepfield Defender. SPM has helped us cut DDoS detection and mitigation time by (at least) a factor of two.
Like NetFlow, SPM relies on using a small subset, or sample, of the packets traversing a router. The big difference is that with SPM, each sampled packet is forwarded immediately for processing instead of being cached on the router. This approach dramatically reduces “Time to Drop First Byte” by eliminating flow export latency.
The conventional method relies on Generic Routing Encapsulation (GRE) tunneling to export these sampled packets. The routers don’t export entire packets, but rather a configurable length, typically 256 bytes.
Our own shim encapsulation provides an even better method. In this case, Nokia Service Routers insert a shim header over a User Datagram Protocol (UDP) datagram, followed by the sampled packet. This enables more granular reporting (e.g., on a per-interface basis) for forwarded packets as well as packets dropped by the router filter entries. This is especially important for measuring the effectiveness of a DDoS mitigation effort. Shim encapsulation is also far easier to configure and operate than conventional GRE/layer 2 port mirroring approaches.
You may be wondering: Is it really useful to get only a small fraction of the packets a router forwarded instead of using the standard sampled flow data that network engineers are used to?
The short answer is a resounding yes.
We get actionable data in a partial packet that we don’t get in NetFlow. For example, we can identify spoofed traffic with information from the TCP Sequence and Acknowledgement numbers included in the TCP header. Or we can distinguish potentially invalid Domain Name System (DNS) requests meant to overwhelm an authoritative nameserver. As an added benefit, we also reduce the bandwidth impact from the routers to the central Deepfield Defender instance.
So what does this mean for you, as someone dealing with DDoS attacks at scale?
For one, SPM detects DDoS traffic much faster than NetFlow-based systems. As shown in Figure 1, our Time to Drop First Byte is 30 seconds or less. Our customers often see even faster reaction times.
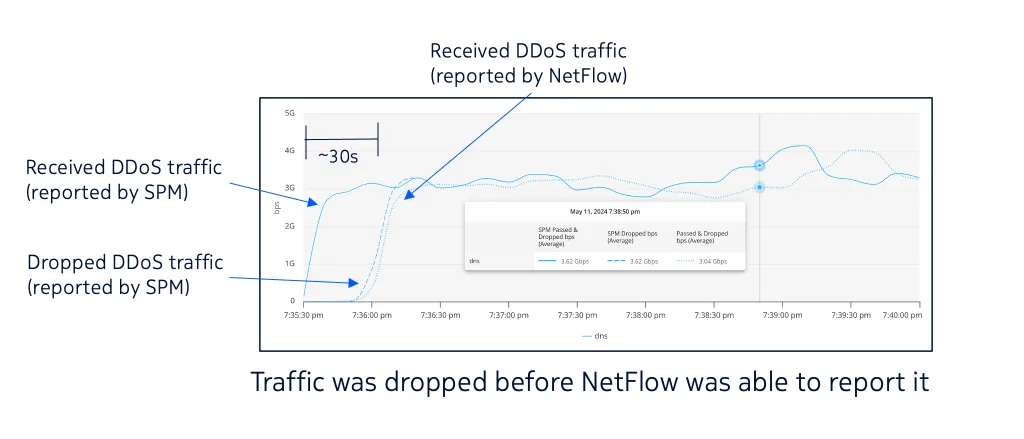
Figure 1. Comparing SPM and NetFlow (active flow timeout 60 s, inactive flow timeout 30 s)
SPM also enables you to do more with your existing router infrastructure instead of continuing to spend on expensive, dedicated scrubber appliances. As I mentioned in an earlier post, it’s all about adding new layers of intelligence to your routers!
To learn more, check out our video playlist “DDoS security with Nokia Deepfield” or come to see our DDoS security solution “in action” at the upcoming SReXperts events – the first one in 2024 is coming up on June 4-6, in Palma, Spain.








