Security standards
Strengthening network security postures

How to elevate a network’s security posture?
Networks are the backbone of a more inclusive and sustainable growth of the global economy. Achieving this goal requires networks that are trustworthy, secure and resilient. The security of networks is realized through a comprehensive approach that involves four major stages.
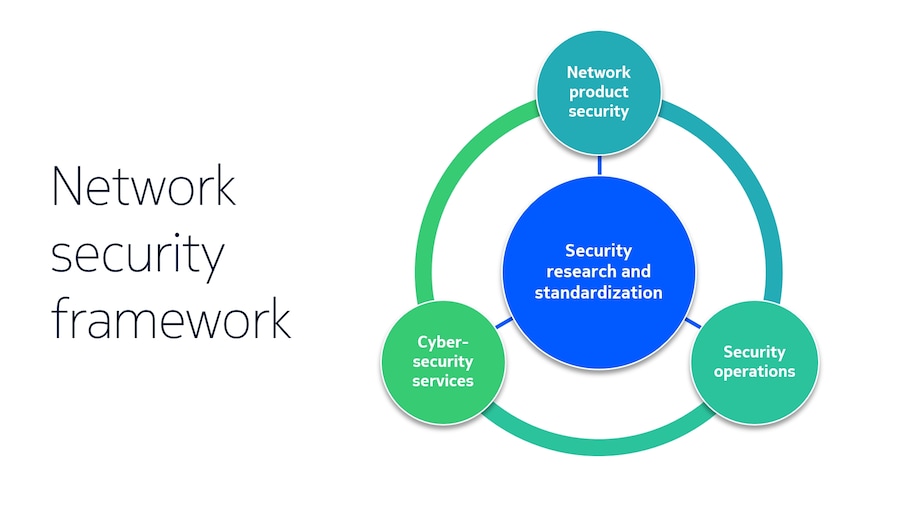
Security research and standardization
Central to the framework is a foundation that begins with thorough research and meticulous standardization. Our security research and standardization efforts directly influence the development and deployment of products, and the associated services that Nokia offers. The lessons learned from the market continuously inform and enhance our research and standardization efforts.
Network product security
Second, for the development of network products and solutions, Nokia follows its “design for security” process (DFSEC). DFSEC focuses not only on the security of the product but also on the security of the product design environment to prevent so-called supply chain attacks. Supply chain attacks involve compromising a trusted product by inserting malware or backdoors during its development or distribution process Nokia products are tested and audited on security levels in line with the GSMA Network Equipment Security Assurance Scheme (NESAS) standard, ensuring product security.
Security operations
Third, Nokia also offers a comprehensive and unique portfolio of network security products and solutions to protect networks from attacks. Nokia’s product portfolio, including NetGuard Cybersecurity Dome and Deepfield, provides security monitoring, threat incident response, identity access management and DDoS detection and mitigation and more. These products play a crucial role in security operations.
Cybersecurity services
Fourth, the actual network deployment leverages state-of-the-art secure configuration designs and secure operations and maintenance (OAM), which ensure resilience against cyber-attacks. To guarantee secure deployment and operation of networks, the security framework of the Nokia services and supply chain are aligned with information security standards such as ISO/IEC 27001. Nokia consultants and our dedicated cybersecurity testing lab, ASTaR lab, provide the expertise, tools and best practices needed to prepare customers for worst-case scenarios. Nokia threat intelligence reports provide unique insights for all our stakeholders. These cybersecurity services help organizations safeguard their network, maintain the confidentiality, integrity, and availability of their data, and reduce the risk of cyber-attacks.
Why are network security standards needed?
Nokia is a strong advocate of open and global security standards as they contribute to the reliability of the specified security features. For many years, Nokia has been at the forefront of researching and standardizing novel secure and resilient algorithms and protocols. Our work covers aspects such as authentication, encryption, network access control, secure communication protocols, certification and compliance with regulatory requirements. We actively participate in the most relevant global and regional organizations, councils and fora such as 3GPP, IETF, ORAN Alliance, GSMA, NIST, ETSI, ENISA, FCC CSRIC, ATIS, TSDSI and others. Being actively engaged in these organizations, we possess the expertise to integrate various standards cohesively, ensuring an all-encompassing defense-in-depth approach to the end-to-end network.
Network security cannot be approached as a standalone solution. Today's networks are highly interconnected, and they encompass AI and cloud technologies. They are becoming more programmable, allowing for third-party control over network capabilities and exposure of valuable data and services to applications and developers. Resources are shared across multiple stakeholders and extend beyond national boundaries. This open interconnectedness necessitates a holistic and continuous security strategy that encompasses the entire network.
3GPP
3GPP
3rd Generation Partnership Project (3GPP) is responsible for the creation and maintenance of standards for mobile access technologies, system and services, including 5G and the, in-development, 6G. Since 2021, Nokia’s Suresh Nair has been the chair of the Service & System Aspect Working Group 3 (SA3). SA3 is responsible for security in the 5G system. The primary objectives of SA3 includes defining the requirements and specifying the architectures and protocols for security and privacy. SA3 is also responsible for ensuring the availability of cryptographic algorithms that are part of the specifications.
Since the introduction of 5G, SA3 has been responsible for security requirements for the whole 3GPP system including devices, RAN and network, protecting the network from fake devices, protecting the devices from fake networks, and for network domain security. Within his role as chair, Suresh Nair has published multiple articles in recent 3GPP newsletters to share some of the latest standards as defined in SA3 (Security Assurance Specifications, Rel-18 security feature summary and Authentication and Key Management for Applications (AKMA) in 5G).
Nokia has been an active contributor in the past to many new security standards within 3GPP. The non-exhaustive list includes the authentication procedures for 4G and 5G, end-to-end network slicing security, security for private networks (5G NPN), and the smooth migration of Diameter to the 5G service-based architecture (SBA) to, for instance, roaming networks.
Today, Nokia is actively involved in many security studies and making many contributions to SA3. Some examples are the focus on 256-bit confidentiality and integrity algorithms for the air interface, the zero-trust study, authentication and key management for applications, bidding down attacks, and many other security studies and items coming from other working groups' studies.
Nokia has been leading the 3GPP standardization of public key infrastructure (PKI), which is now the baseline for the GSMA PKI work. Asymmetrical key encryption will be vulnerable, to being broken by quantum computers, hence our work to standardize post-quantum security. Nokia is also leading other areas of security standardization work, for example, non-3GPP access, non-seamless WLAN offload (NSWO), satellite, and energy saving.
Fewer than ten individuals globally have received the 3GPP Lifetime Achievement Award. Nokia’s security expert Günther Horn won the award in 2018, recognizing how he has underpinned the expertise and contributions that Nokia has made and continues to bring to SA3.

GSMA
O-RAN Alliance
IETF
North American fora
European fora
Indian fora
3GPP
3rd Generation Partnership Project (3GPP) is responsible for the creation and maintenance of standards for mobile access technologies, system and services, including 5G and the, in-development, 6G. Since 2021, Nokia’s Suresh Nair has been the chair of the Service & System Aspect Working Group 3 (SA3). SA3 is responsible for security in the 5G system. The primary objectives of SA3 includes defining the requirements and specifying the architectures and protocols for security and privacy. SA3 is also responsible for ensuring the availability of cryptographic algorithms that are part of the specifications.
Since the introduction of 5G, SA3 has been responsible for security requirements for the whole 3GPP system including devices, RAN and network, protecting the network from fake devices, protecting the devices from fake networks, and for network domain security. Within his role as chair, Suresh Nair has published multiple articles in recent 3GPP newsletters to share some of the latest standards as defined in SA3 (Security Assurance Specifications, Rel-18 security feature summary and Authentication and Key Management for Applications (AKMA) in 5G).
Nokia has been an active contributor in the past to many new security standards within 3GPP. The non-exhaustive list includes the authentication procedures for 4G and 5G, end-to-end network slicing security, security for private networks (5G NPN), and the smooth migration of Diameter to the 5G service-based architecture (SBA) to, for instance, roaming networks.
Today, Nokia is actively involved in many security studies and making many contributions to SA3. Some examples are the focus on 256-bit confidentiality and integrity algorithms for the air interface, the zero-trust study, authentication and key management for applications, bidding down attacks, and many other security studies and items coming from other working groups' studies.
Nokia has been leading the 3GPP standardization of public key infrastructure (PKI), which is now the baseline for the GSMA PKI work. Asymmetrical key encryption will be vulnerable, to being broken by quantum computers, hence our work to standardize post-quantum security. Nokia is also leading other areas of security standardization work, for example, non-3GPP access, non-seamless WLAN offload (NSWO), satellite, and energy saving.
Fewer than ten individuals globally have received the 3GPP Lifetime Achievement Award. Nokia’s security expert Günther Horn won the award in 2018, recognizing how he has underpinned the expertise and contributions that Nokia has made and continues to bring to SA3.

GSMA
The Global System for Mobile communication Association (GSMA) is the global industry organization representing the interests of mobile network operators and related industries across the ecosystem.
The GSMA Fraud and Security Group (FASG) deals with security aspects in cellular networks and provides a toolkit to help stakeholders identify, map, and mitigate risks. FASG consists of several working groups; in many of them Nokia is an active contributor, especially in task forces relating to 3GPP-specified 5G security.
Nokia initially presented the 5G security enhancements of 3GPP Rel-15 in FASG and has since been a key liaison between 3GPP and GSMA on security topics. Three examples of Nokia contributions in GSMA FASG are: the "5G Security Guide" (FS.40) developed in the 5G Security Task Force (5GSTF), the "Key Management for 4G and 5G Inter-PLMN Security guide" (FS.34) written by the roaming and interconnect group (RIFS/DESS) and the "Baseline Security Controls document" (FS.31) of the architecture group (FSAG).
With two active expert panel members, Nokia plays a pivotal role in FASG supporting the success of the GSMA Coordinated Vulnerability Disclosure (CVD) program. The program allows effective vulnerability reporting by researchers, security professionals, and ethical hackers. It enables discrete information sharing on security vulnerabilities within the mobile industry and initiating necessary steps for improvements regarding reported cases.
The GSMA Network Equipment Security Assurance Scheme (NESAS) defines an industry-wide security assurance framework, covering security requirements on vendor’s product development and product lifecycle processes as well as a methodology for evaluating the security of network products. Nokia contributes to both the GSMA FASG NESAS group and 3GPP SA3 working group, the latter defining security assurance specification (SCAS) test cases.
The GSMA FASG and Network Group (NG) jointly revisited 5G roaming security in the so-called 5GMRR working group covering the interests of all mobile communication ecosystem players. Nokia ensures that the "5G roaming guidelines" (NG.113) combine 3GPP-specified 5G security architectures together with GSMA-defined additional architectures.
The FASG Post-Quantum Telco Network (PQTN) Taskforce publishes documents on the impact of post-quantum cryptography (PQC) in the telecom industry, with Nokia contributing its expertise, including leading the work in IETF PQC. Nokia contributed to the PQC Guidelines for Telecom Use Cases.
The FASG 5G Public Key Infrastructure (5GPKI) Working Party addresses the need for an industry-standardized solution for PKI management. Nokia is leading standardization on PKI automation on the 3GPP front as a baseline for the work in GSMA.

O-RAN Alliance
The O-RAN Alliance is dedicated to transforming radio access networks (RAN) with a focus on intelligence and openness. It seeks to guide the mobile industry toward an innovative ecosystem supporting a multi-vendor, interoperable, and autonomous RAN, which reduces costs, improves performance, and creates greater agility.
Working Group 11 within the Alliance is responsible for developing security specifications across the O-RAN architecture and interfaces. Nokia plays a leading role in this group, acting as the primary contributor and rapporteur on several work items. In the area of security event logging, we are establishing enablers for audit and continuous zero-trust monitoring. For near-real-time RIC security, we are defining security tests for input validation and error handling and examining authorization requirements. Additionally, we focus on securing AI/ML components throughout the O-RAN architecture, including the SMO, non-RT RIC, near-RT RIC, rApps, and xApps, with a special emphasis on threat modeling and assessment to protect against AI/ML attacks such as O-RAN poisoning. Poisoning involves introducing malicious or manipulated data into a network's AI/ML training process to disrupt its performance.
Nokia, together with three other companies, is one of the driving forces to ensure that the security specifications of WG11 will be published soon through the ETSI PAS (publicly available specifications) process. Making the O-RAN specification available as an ETSI standard will provide the additional endorsement sought by both commercial and public sector entities in various countries.
Nokia also holds a co-chair position in the nGRG research stream 04 (RS04), which focuses on the security considerations of evolving next-generation networks. Central to this focus are the trustworthiness, security and privacy aspects. Nokia is contributing to understanding the 6G security threat landscape, examining threats in "6G sensing" use cases. Nokia has also researched and is contributing to platform security, specifically in trusted computing with attestations. In the realm of privacy, topics include homomorphic encryption and differential privacy, where Nokia’s leading researchers have been actively involved. Nokia played a significant role in the area of quantum security, contributing to the pilot research report released at the end of 2023.
The O-RAN Alliance publicly announced its pursuit of zero-trust architecture (ZTA) with the publication of a ZTA white paper where Nokia was also an active contributor. Recently, Nokia became rapporteur of the continuous security monitoring to drive the study and involvement in ZTA.

IETF
The Internet Engineering Task Force (IETF) is a global, open organization that develops and promotes internet standards, particularly the standards that comprise the internet protocol suite (such as TCP/IP). The standards, as specified in IETF, have an impact on many other standards-developing-telecom-network-related bodies such as 3GPP.
The technical work of the IETF is done in working groups, which are organized by topics into different areas, such as routing, transport, security, and operations. The security area is the home for working groups focused on security and privacy protocols.
Recently Nokia has been very active in standardizing the use of post-quantum cryptography (PQC) in internet security protocols. We have co-authored a whopping number of 10 internet drafts from Q2 2023 to Q2 2024, several of which have been accepted by the working groups (WGs) and one is enroute to become a request for comment (RFC) soon. Some key internet drafts Nokia has contributed include PQC for engineers, the hybrid public key encryption in JOSE, the PQ/T hybrid key exchange in JOSE and COSE, and post-quantum key encapsulation mechanisms for COSE and JOSE. These were followed by Signature Authentication in the IKEv2 using PQC in IPSec, PQC recommendations for internet applications for TLS in the UTA WG, and PQC enhancements to the security of the Extensible Authentication Protocol (EAP) using the EAP-AKA prime in the EMU WG (Hybrid PQ, PQ).
Beyond proposals related to PQC, Nokia is also actively contributing to several other security-related specifications such as a proposal to protect DNS queries against pervasive monitoring and tampering and a proposal to include attestation evidence to X.509 PKI and Certificate Signing Requests (CSRs). Nokia also proposed a solution to allow a network security service to identify unexpected TLS (Transport Layer Security) usage, which can indicate the presence of unauthorized software, malware, or security policy-violating traffic on an endpoint.

North American fora
The Communications Security, Reliability, and Interoperability Council (CSRIC) provides recommendations to the US Federal Communications Commission (FCC) to ensure the security, reliability, and interoperability of communications systems. Nokia has actively participated in previous councils, sharing its security expertise to establish strong recommendations. Nokia is a council member of CSRIC IX, established in June 2024, and engages in the AI security and 6G security risks working groups.
The mission of the President’s National Security Telecommunications Advisory Committee (NSTAC) is to offer the US government the best industry advice in security and telecommunications. Nokia is an active participant to these studies and has made numerous contributions including the NSTAC report to the president on “Addressing the Abuse of Domestic Infrastructure by Foreign Malicious Actors”.
The Alliance for Telecommunications Industry Solutions (ATIS) brings together leading global ICT companies to advance the industry’s priorities by setting standards and solutions. Nokia contributed to several security-related groups such as the ATIS 5G Supply Chain group and the ATIS Enhanced Zero Trust & 5G group and is currently participating in the ATIS 5G Secure Profile group.
The ATIS Next G Alliance is an initiative to advance North American wireless technology leadership through the private sector. Under Nokia’s leadership, with Amitava Ghosh as chair, the National 6G Roadmap working group drove six audacious goals, the first and foremost being trust, security, and resilience.
The EU-US Trade and Technology Council, established in 2021, serves as a forum for the US and the EU to coordinate on global trade, economic and technology issues and to deepen transatlantic relations. Nokia has played a key role in developing the joint document on the Beyond 5G/6G Roadmap, which includes discussions on trustworthiness and cybersecurity.
The Communications Sector Coordinating Council (CSCC) collaborates with US government partners to protect the nation’s critical communications infrastructure and ensure that networks and systems are secure, resilient and rapidly restored after disasters. Nokia joined the council to share its extensive expertise in resilient networking.
5G Americas advocates for the advancement of 5G and the transition to 6G across the Americas. Nokia is an active participant in this industry trade organization and has contributed to many white papers such as the 3GPP Technology Trends, which zooms in on trustworthy AI and new security enhancements in 5G.
The National Institute of Standards and Technology (NIST) is part of the US Department of Commerce. NIST develops cybersecurity standards, guidelines, best practices, and other resources to meet the needs of US industry, federal agencies and the broader public. The National Cybersecurity Center of Excellence (NCCoE) launched the 5G Cybersecurity Project to identify 5G use case scenarios and to demonstrate how 5G architecture components can provide security capabilities. Nokia is the main 5G solutions provider to collaborate with NIST. Nokia actively participated in the 2023 Webinar on 5G Cybersecurity. In 2016, NIST initiated a process to solicit, evaluate and standardize one or more quantum-resistant public-key cryptographic algorithms. Nokia participated in a benchmarking of Post-Quantum TLS1.3, which was recently shared with NIST and submitted the ALTEQ digital signature which was accepted as a full submission and is undergoing additional rounds of review currently. In the summer of 2024, NIST released the new FIPS 203, 204 and 205 algorithms.



European fora
The European Telecommunications Standards Institute (ETSI) provides members with an open, inclusive and collaborative environment that supports the timely development, ratification and testing of globally applicable standards for ICT-enabled systems, applications and services. Nokia’s Colin Willcock is the elected vice chairman of the board. The Technical Community Cybersecurity (TC Cyber) provides market-driven cybersecurity standardization solutions and offers advice and guidance to users, manufacturers, network operators, infrastructure and service providers, and regulators. These key focus areas are outlined in the TC Cyber roadmap.
In the recent past, Nokia has been a significant contributor to, for instance, a specification to ensure secure computing in a network function virtualization (NFV) environment by looking to the authentication and attestation procedures.
The European Network and Information Security Agency (ENISA) is the EU's dedicated agency for achieving a high common level of cybersecurity across Europe. Established in 2004 and bolstered by the EU Cybersecurity Act, ENISA contributes to the EU’s cyber policy, enhances the trustworthiness of ICT products, services and processes through cybersecurity certification schemes, cooperates with member states and EU bodies, and helps Europe prepare for future cyber challenges. Nokia is providing expertise in the different work streams upon ENISA’s request. Among several working groups, Nokia notably contributed to the ad-hoc working group on 5G Cybersecurity Certification.
The EU NIS 2 directive provides horizontal risk-management and reporting requirements for entities across the EU that provide critical services such as banking, energy or telecom. Whereas the NIS 2 focuses on securing the networks and systems, including their supply chains, to prevent incidents, the EU Cyber Resilience Act ensures that the deployed hardware and software complies with appropriate security controls.
The European Commission has published a standardization request towards CEN (the European Committee for Standardization or in French, la Comité Européen de Normalisation) / CENELEC (the European Committee for Electrotechnical Standardization or in French, la Comité Européen de Normalisation Électrotechnique) to draw up and adopt European standards or European standardization deliverables in support of EU legislation and, more particularly, the EU Cyber Resilience Act (CRA) policy. The ambition is to ensure there are harmonized rules with respect to cybersecurity requirements when bringing to European markets products or software with a digital component. The CEN/CENELEC Working Group 9, with support of many industry partners, started to address this request in Q3 2024.



Indian fora
The Telecommunications Standards Development Society India (TSDSI) plays a crucial role in developing, promoting, and standardizing India-specific telecom and ICT requirements and solutions. TSDSI also advocates for Indian innovations on global standards platforms. Nokia, represented by Saurabh Khare, chairman of TSDSI's security work group (WG1), is actively involved in various security initiatives within TSDSI.
Nokia's contributions encompass significant ongoing projects such as the 6G security enabler study, post-quantum cryptography (PQC) study, AI/ML security considerations, and the development of India-specific security ciphering algorithms. These initiatives highlight Nokia's leadership in shaping security discussions and requirements within TSDSI, primarily concentrating on the preliminary steps towards 6G standardization.
Meanwhile, India’s Department of Telecom (DoT) is progressing with the development of a security certification scheme named ITSAR (Indian Telecom Security Assurance Requirements) for telecom products through the National Centre for Communication Security (NCCS). This scheme aims to harmonize Indian security standards with global benchmarks, a process in which the DoT actively participates in fora like 3GPP. Nokia is closely collaborating with the DoT to support this initiative, aligning Indian security certification practices with global standards. This collaborative effort aims to enhance India's capabilities in telecom and ICT security, ensuring both national security requirements and global compatibility.


Discover more
Video
Nokia 6G Livestream: Security Blueprint
Article
Blog

Article

Article

Article

Article

White paper