Today’s challenge
Several demonstrations of intercepted sensitive communications highlight the difficulty of protecting high risk infrastructure.
End-to-end encryption (E2EE) for conference systems has become an industry standard and is widely implemented in applications such as Zoom, Wire, Discord and other platforms. However, audio calls introduce unique challenges. Each participant’s audio must be captured and combined into a single stream, a process known as audio mixing.
In traditional (non-E2EE) conference systems, such as Microsoft Teams, Google Meet, VoLTE, audio mixing happens on a central server, which has full access to the unencrypted audio. In contrast, with E2EE conferencing systems, each audio stream must be encrypted locally and sent to every participant in the group call. End-to-end audio encryption protects privacy but creates major challenges:
- Poor traffic scalability: Without the ability to mix audio streams centrally, a peer-to-peer mesh is used between participants. As a result, the network traffic complexity grows quadratically as the number of participants increases.
- Speaker privacy overhead: To hide who is speaking, all participants must receive and decrypt every other participant’s stream before mixing locally.
- Audio synchronization: Local audio mixing makes synchronizing audio from multiple encrypted streams complex and inconsistent across participants.
- Loss of advanced server-side enhancements: Many audio techniques, such as mixing, denoising, normalization, and dynamic range compression are typically applied on the server using advanced proprietary algorithms. This requires access to decrypted audio content on the central server and thereby breaks E2EE.
Our solution
Our End-to-End Encrypted Audio Conferencing combines the privacy of E2EE with the benefits of server-side mixing, without ever exposing your audio to providers.
Using quantum-safe homomorphic encryption, we enable high-quality, scalable group calls where each participant sends one encrypted stream to and receives encrypted stream from the server, regardless of how many people join. This keeps network usage predictable and efficient, while also hiding who is speaking from passive network observers. With our solution, your voice stays encrypted, not just in transit and at rest, but even while it is being processed.
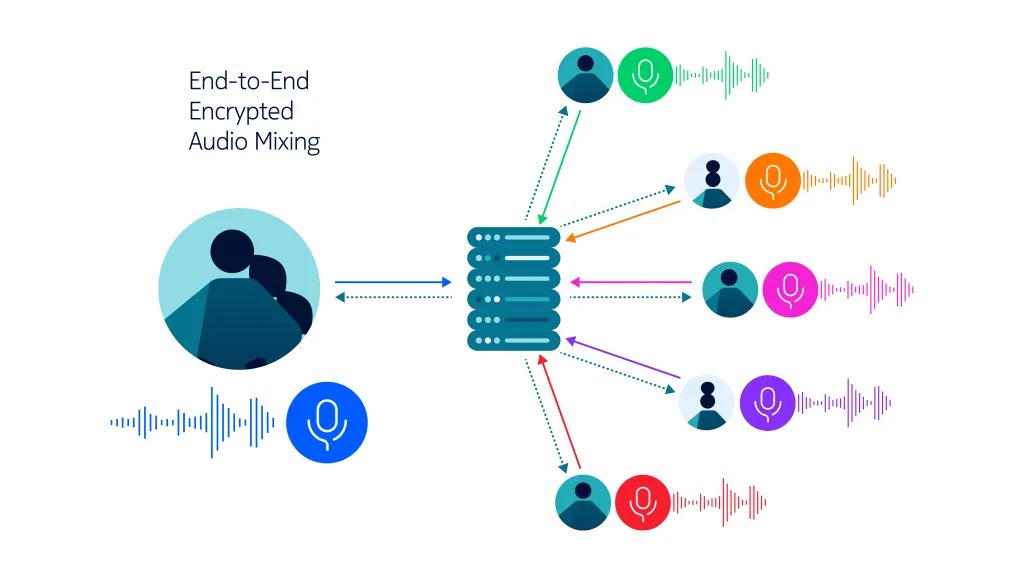
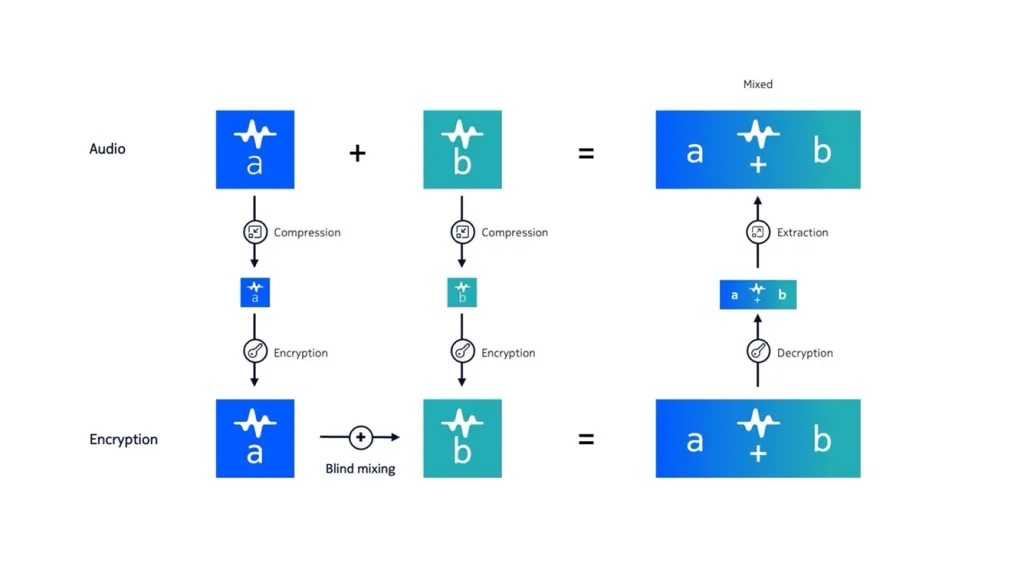
With our End-to-End Encrypted Audio Conferencing, each participant’s audio is first compressed into a compact, homomorphism-preserving form, then encrypted and finally sent to the server. The server homomorphically adds the encrypted streams, blindly mixing them into a single ciphertext. Participants decrypt and decompress the result locally to obtain a high-quality audio mix for playback
Key technology enablers
Blind audio mixing
Encrypted audio streams are processed and mixed on the server using state-of-the-art, quantum-safe homomorphic encryption (HE) techniques. The server never has access to the unencrypted audio content at any stage
Homomorphism-preserving audio compression
Our compression method reduces plaintext audio size up to 128x before encryption, addressing the expansion challenge common in HE schemes. Additionally, it preserves additive homomorphism, enabling efficient mixing of compressed encrypted audio streams
Our vision
We believe the internet should run on infrastructure you don’t have to trust. That’s why we make secure computation a core architectural principle, keeping your keys out of the infrastructure and your data out of reach to providers. This ensures that the servers processing your data can never decrypt it which drastically reduces the risk from potential breaches or zero-day vulnerabilities.
For over a century, Bell Labs engineers have been improving communications across every medium, from copper phone lines to fiber optic cables, from satellite links to cellular networks. Many have worked to remove noise for maximum clarity and performance. But over the years, engineers have also carefully designed noise - the kind that shields messages from interception and protects the people who send them. From SIGSALY to our latest End-to-End Encrypted Audio Conferencing, we are extending this tradition to offering a scalable, secure solution for the next generation of zero-trust services.
Project members
Publications
- Emad Heydari Beni, Lode Hoste, Geert Heyman, Paschalis Tsiaflakis, Barry van Leeuwen, Robin Geelen, Marc Rivinius, Claudia Bartoli, ”QRYPT: End-to-End Encrypted Audio Calls via Blind Audio Mixing”. Real World Crypto 2025. (https://youtu.be/PMmBfXC1HQE, https://iacr.org/submit/files/slides/2025/rwc/rwc2025/152/152_slides.pptx )
- Emad Heydari Beni, Lode Hoste. “End-to-End Encrypted Audio Calls via Blind Audio Mixing”, Security Seminar Series, Cambridge University. (https://www.cl.cam.ac.uk/research/security/seminars/archive/video/2025-05-27-t231706.html)
Please complete the form below.
The form is loading, please wait...
Thank you. We have received your inquiry. Please continue browsing.








