Ensure a robust AI-native 6G security posture
27 November 2025

Networks occupy a central role in our social and economic infrastructure, making the security of telecommunications exceptionally important, a significance which will only grow with the broader adoption of AI. In the evolution to AI-native 6G, this is reflected by integrating security and privacy within the design principles and technical frameworks that define its comprehensive system architecture.
Building on the foundation laid by 5G, the 6G system architecture is expected to adopt a secure-by-design paradigm. It incorporates security as a fundamental requirement during architecture design and provides adequate frameworks to meet key needs such as privacy preservation, resilience, reliability, automated security, and sustainability.
In its ambition to ensure reliable and adaptive networks, 6G enhances and augments existing 5G security features while developing innovative solutions to address new emerging security challenges. Some of these include quantum-safe cryptography and AI-driven threat management. Looking beyond traditional communications services, the 6G systems must also seamlessly and securely integrate technologies like sensing, digital twins and immersive experiences. 6G must ensure that all devices can securely transition between terrestrial and satellite networks, that AI inference services are accessed safely, and that every device from smartphones, smart glasses to earbuds remains protected. These advancements are critical to enable 6G to deliver and ensure a robust security posture in our hyper-connected world.
This article examines the most relevant security lessons learned from earlier generations, delves into key security principles and requirements, and highlights Nokia's perspective on selected new security aspects of 6G.
Security lessons learned from 5G and earlier generations
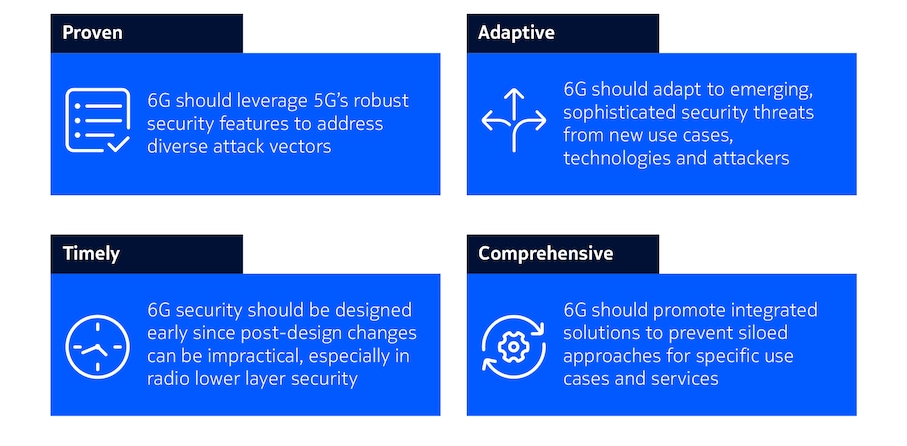
Lessons learned from 5G and earlier generation deployments provide multiple security insights and valuable directions in building the sixth generation of mobile networks, as illustrated in figure 1.
Figure 1. Security lessons from earlier generations shaping AI-native 6G
In many ways, 5G has been successful in addressing the security challenges that were most relevant during its design phase. For instance, 5G provides a strong, flexible and access-agnostic authentication framework using 5G Authentication and Key Agreement (AKA) and Extensible Authentication Protocol (EAP) mechanisms. It also prevents packet manipulation and injection attacks in the air interface by protecting user plane integrity. For roaming control and user plane security in interconnection, it uses Secure Edge Protection Proxy (SEPP) and Inter-PLMN User Plane Security (IPUPS). The concept of Subscription Permanent Identifier (SUPI) concealment ensures subscription identity privacy. With the introduction of 6G, it is essential to guarantee that security evolves by building on these robust security features.
Still, leveraging and complementing security features from 5G will not be sufficient. 6G will encompass new, emerging technologies, which inherently expand the threat surface together with the introduction of new use cases and applications. Therefore, 6G will also need to be ready to adapt its security architecture to incorporate mechanisms that can cope with this new and evolving threat ecosystem.
Technology has not stood still since the introduction of 5G, new threats and factors have emerged that will also impact the overall threat landscape for 6G. Advances like AI and quantum computing pose future risks that have to be anticipated in today’s 6G design. One prominent threat is that a Cryptographically Relevant Quantum Computer (CRQC) becomes capable of breaking asymmetric cryptography by running Shor’s algorithm. The arrival of such computers may render traditional cryptographic systems, particularly asymmetric encryption, obsolete, thus exposing critical digital infrastructures and economies to significant security risks. While this threat is estimated to be 10 to 25 years away, the threat is already present today due to "harvest now, decrypt later" attacks, where malicious actors collect encrypted data transmitted today, e.g., over the radio link, and store it to decrypt it in the future using cryptographically relevant quantum computers. This example underscores that security must be designed early and in a timely manner, as post-design changes can be impractical, especially in radio lower layer security.
As another lesson learned, the distributed development of edge cloud specifications during 5G standardization across 3GPP working groups such as SA2 and SA6, and ETSI MEC led to the absence of a unified security framework. A similar situation developed regarding the protection of exposure services. Network Exposure Function (NEF) and the Common API Framework (CAPIF), both defined by 3GPP to standardize how network APIs are discovered, exposed, and consumed, require two different security solutions. In order to prevent such siloed approaches, comprehensive and integrated solutions should be preferred.
Security principles and resulting system characteristics
There is a high expectation by end-users, enterprises, telecommunications providers, and regulators that 6G will provide a fully trustworthy communication infrastructure. Trust grows where privacy is protected, security is assured, and technology is built from the ground up to incorporate privacy and security principles.
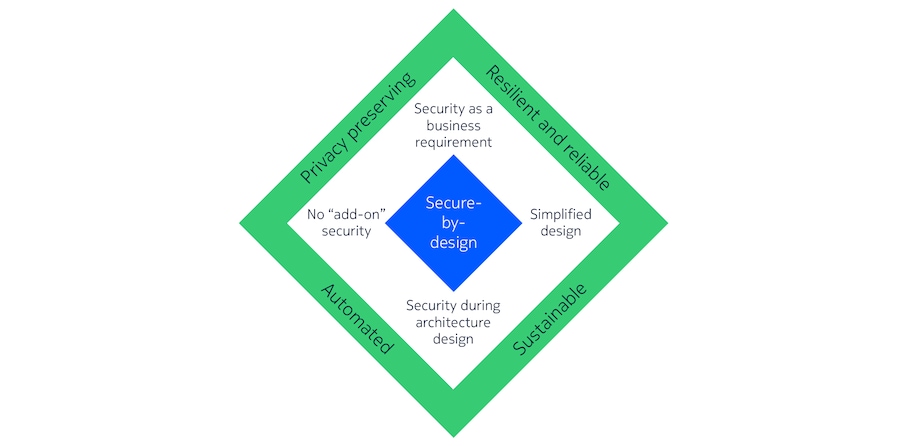
When developing new standards, Nokia treats network security as a strategic priority. Our design philosophy blends the distilled wisdom of past experience with anticipation of upcoming developments. The analysis of lessons learned from 5G and previous generations, as well as the new security demands from users, telecommunications providers and society, have led Nokia to a secure-by-design paradigm. This paradigm covers four main principles as outlined in the inner part of figure 2. First, it ensures that security is not an ‘add-on’ or afterthought but must be designed as a foundational principle guaranteeing that the networks of tomorrow are ready to support emerging digital societies. Second, security considerations are integrated into the architecture design. Third, security is treated as a fundamental business requirement in every stage of a system's lifecycle from initial conception, standardization, deployment, operations, to maintenance. Finally, security should also adhere to the lean and simplified design principle as followed in the overall 6G system architecture.
Figure 2. Security principles and resulting 6G system characteristics
Realizing this secure-by-design paradigm will result in four main characteristics (outer shell of figure 2) that 6G will incorporate to serve as society’s fully trusted communication system.
The privacy preserving characteristic has become even more critical with the planned proliferation of AI and data usage in 6G. Confidentiality of both machine learning (ML) models and training and inference data must be ensured. Privacy preservation for sensitive data and models must be considered for the entire AI lifecycle.
Besides AI, there are new use cases such as sensing, digital twins, XR, immersive experience, and avatar communications, which will involve data in need of privacy protection. This will require robust user consent management frameworks for dynamic update and revocation of user consent. It needs to be complemented by regular auditing to align with regulations.
6G will be a part of our society’s critical infrastructure and, hence, must be resilient and reliable. It must ensure the availability of essential services by designing protective measures to deal with failures. These measures should allow continued access to main services during disruptions and maintain acceptable service levels, even under stress, for the essential operational capabilities of the network. The goals should be to fail safely and recover quickly, so that faults and adverse conditions do not impact critical services and prioritized applications. To be able to deliver such resilience, 6G needs to recognize anomalies and adapt proactively. This requires self-awareness of the network state, identification and prediction of potential failures, reconfiguration capabilities as well as the ability to learn from the past and self-optimize for improved resilience.
Such dynamic adaptation capabilities necessitate automated security, a main tenet of the Zero Trust Architecture’s “never trust, always verify” approach. This requires continuous monitoring and verification with holistic, situational insights into network assets and operations, driven by dynamic policies for continuous verification of identities as well as fine-grained and contextual access control. Automation of security is also essential for predictive threat detection and active response. Achieving 6G dynamic security will, further, require proactive compliance and security assurance through threat intelligence, detection and hunting. This, in turn, requires automated security compliance testing and predictive runtime attack.
Last but by no means least, a crucial 6G characteristic is embedded sustainability. Many of the security characteristics detailed above will bring additional computational and communication burdens, which have energy and environmental implications. Lightweight cryptography algorithms, energy-aware selection of security features, or lean security solutions can contribute to environmental sustainability goals. There are also societal aspects to sustainability that are critical requirements for the success of 6G, thereby mandating, amongst others, trustworthy and responsible use of AI technology with fairness, transparency and robustness. Among the most important requirements are compliance with regulatory frameworks around data protection and privacy preservation and alignment with ethical guidelines and societal values.
New aspects of 6G security: the Nokia view
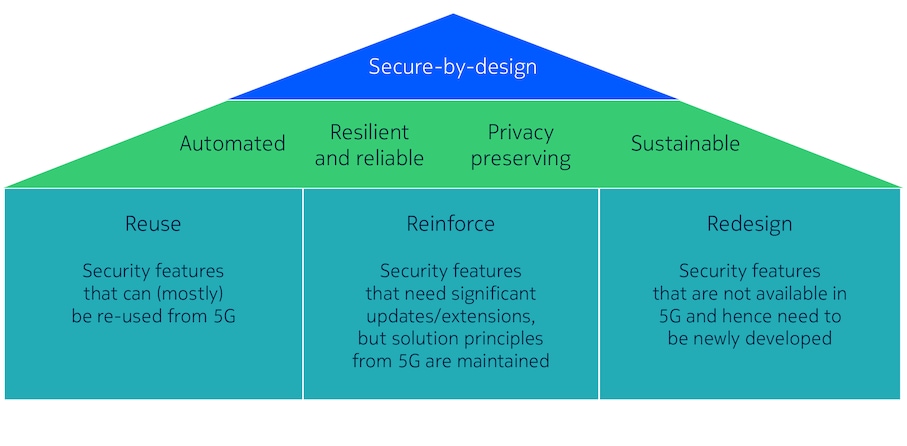
Just like the security of having a sound roof over our heads, securing 6G networks requires a robust structure. Nokia’s security structure comprises three pillars: reuse, reinforce and redesign to address both existing and novel security challenges (see figure 3). These pillars support the secure-by-design paradigm we’ve described above. By leveraging proven security features from 5G (reuse), enhancing existing mechanisms where necessary and possible (reinforce), and developing new solutions (redesign), the Nokia 6G security house ensures a comprehensive approach to safeguarding the network.
Figure 3. The three pillars of the Nokia AI-native 6G security house
In the following, we describe a selection of Nokia-proposed 6G security solutions. They illustrate how key components from the three pillars of our 6G security house jointly realize the secure-by-design paradigm and protect us from emerging security challenges in 6G.
Quantum-safe encryption and integrity protection
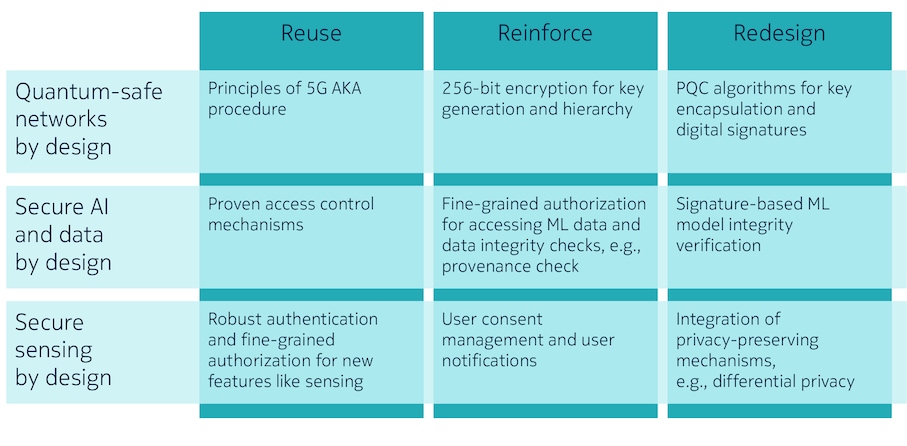
Quantum computing introduces significant vulnerabilities to existing cryptographic protocols, which also impact encryption and integrity protection in various parts of the networks, e.g., concealment of the SUPI. These threats arise from quantum algorithms like Shor’s, which can particularly compromise traditional asymmetric encryption methods. While the 5G AKA (Authentication and Key Agreement) procedure uses symmetric keys and, hence, is less vulnerable to quantum attacks, other parts of 5G security such as TLS (transport layer security) in the service layer and IPsec in backhaul do use asymmetric cryptography.
To mitigate these risks, transitioning to quantum-safe encryption and integrity protection mechanisms is essential. An important solution involves transitioning to stronger and longer keys in the protection of the air interface between the UE and the base station as well in the protection of the interface between UE and the Core. Algorithms like AES (Advanced Encryption Standard) as well as SNOW and ZUC, the latter two being stream ciphers designed for secure communication in mobile networks, should be used with keys of 256-bit length. The adoption of 256-bit algorithms in key-generation and key hierarchy processes provides enhanced cryptographic strength against quantum and classical attacks. Additionally, the integration of Post-Quantum Cryptography (PQC) algorithms, as proposed by the National Institute of Standards Technology (NIST), is crucial for addressing the vulnerabilities of current asymmetric cryptographic schemes. For Key Encapsulation Mechanisms (KEMs), algorithms such as ML-KEM (Module-Lattice KEM, formerly Kyber) or HQC (Hamming Quasi-Cyclic) can be employed, while ML-DSA (Module-Lattice Digital Signature Algorithm, formerly Dilithium) or SLH-DSA (Stateless Hash-Based Digital Signature Algorithm, formerly SPHINCS+) are recommended for digital signatures.
Additionally, Nokia proposes adopting AEAD (authenticated encryption with additional data) for non-access stratum (NAS) and access stratum (AS) procedures. AEAD combines encryption and integrity protection in one operation, thus optimizing performance.
Security for AI and data
The accelerated integration of AI capabilities in various functions of the 6G network will enable, for instance, new levels of radio performance and automation in network operations. At the same time, they introduce a novel threat surface compared to earlier generations. These novel security issues may affect all stages of the ML-model lifecycle. As an example, in the model training phase, utilization of training data from an unauthorized adversarial source might result in injection of malicious data samples and, hence, produce biased or malicious inference outputs. Further risks might arise by backdoor attacks on ML models, model extraction, or adversarial inputs during the inference phase. This is just a sample of many exploits of AI with potentially disruptive impact on network operations and service availability.
Confidentiality and integrity of collected data is ensured by systematically applying provenance checks, privacy-preserving mechanisms, and anomaly detection before clearing data for model training purposes. Fine-grained, attribute-based access control to training data should be used to verify the model training purpose.
For an ML model, signature-based mechanisms allow for distinct model ownership and integrity verification. During the inference phase, incoming requests can be rate limited and analyzed for anomalous patterns. Sanitizing input data, adding an explainable AI component to the inference results (e.g., by including feature attribution), and closed loop feedback mechanisms regarding inference results (e.g., for detection of adversarial attacks) will further increase security levels.
Finally, AI security also includes aspects of trustworthiness for the data and models used during training and inference time. New methods to address this are maturing and will become applicable to 6G. Depending on the future requirements for integrity, confidentiality and privacy protection, one or more of these methods need to be chosen, among them zero knowledge proof, homomorphic encryption, differential privacy, and multi-party computing to strengthen the trust in AI-supported network operations.
Security and privacy of sensing
As 6G networks integrate sensing capabilities alongside communications (aka Integrated Sensing and Communication or ISAC), robust security and privacy mechanisms become paramount. Sensing operations enable the network to detect and interpret physical environments. They also introduce new vulnerabilities such as unauthorized data access, privacy infringements, and the risk of misbehaving or malicious entities disrupting sensing operations. These threats not only compromise sensitive data (particularly with humans in the area of the sensing operation), they also undermine user trust and the reliability of sensing outputs. Addressing these challenges requires a multi-layered approach that aligns with Nokia’s commitment to secure and privacy-preserving networks.
Nokia’s proposed mitigations focus on three key areas: authentication, privacy preservation and accountability. First, authentication and fine-grained authorization mechanisms, such as policy-based access control, ensure that only verified entities can initiate sensing operations and access generated outputs. Second, privacy concerns are addressed through a combination of consent management, data anonymization, and transparent user notifications. The latter are used to warrant that users are informed about sensing operations occurring in their proximity and that any data collected during these operations is adequately protected. Third, Nokia advocates for robust auditing mechanisms to monitor sensing entities, detect anomalies, and exclude compromised nodes from the network. These measures collectively create a secure sensing framework that mitigates risks and fosters trust in the ISAC service.
Figure 4 summarizes how the proposed 6G security solutions are categorized in terms of reusing existing mechanisms, reinforcing current capabilities, and redesigning elements from scratch. Collectively, these approaches enable a secure-by-design foundation across multiple security areas including quantum-safe networks, AI and data security, and sensing security.
Figure 4. Security features grouped in our pillars
Pivoting to “secure-by-design”
The evolution of AI-native 6G represents a pivotal opportunity to reinvigorate security and privacy in communication networks “by design”. Leveraging lessons learned from 5G, 6G will build upon proven security features such as robust authentication frameworks, user plane integrity protection, and subscription identity privacy. It will also address emerging challenges, including threats from quantum computing and AI. Nokia’s secure-by-design paradigm ensures that security is embedded from the outset, enabling adaptive, comprehensive and sustainable solutions to meet the demands of a hyper-connected world. Addressing key requirements such as privacy preservation, resilience and reliability, automated security and sustainability will serve as the backbone of 6G’s trusted communication infrastructure.
The security advances in 6G will benefit end users, telecommunications providers and enterprises. End users will experience the most cyber-resilient network ever, proactively addressing emerging threats while safeguarding data and privacy, which are key concerns for regulators. Telecommunications providers and enterprises will gain optimized, cost-effective solutions built on Nokia’s secure-by-design paradigm, ensuring high security with manageable complexity. These advancements will drive trust, innovation and operational efficiency across the 6G ecosystem.