Protecting every carriage of the 6G train

Mobile networks are now the backbone of national infrastructure, relied upon by billions of people and devices for secure and dependable connectivity. Yet, as their importance grows, so does their exposure to malicious actors seeking to exploit vulnerabilities.
The stakes in 6G are higher than ever: the anticipated rapid proliferation of connected devices, the surge of new digital services, the rise of AI and agentic communication, the expanding API economy, and increasingly sophisticated cyberattacks are creating an unprecedented threat landscape.
Trust grows where privacy is protected, security is assured, and technology is built to be truly trustworthy. This is why security in 6G cannot be treated as an afterthought. It must be designed as a foundational pillar, addressing both capability-driven risks and technology-driven threats. The challenge, and the opportunity, lies in Nokia’s secure-by-design paradigm that ensures that the networks of tomorrow remain trusted, resilient, and ready to support the digital societies they enable. Nokia’s secure-by-design philosophy is not a feature but a proactive approach to security where security considerations are integrated into every stage of a system's lifecycle, from initial conception, standardization and design to deployment and maintenance. When developing new standards, Nokia treats security as a core business requirement, embedding it throughout the lean architecture design process from the outset.
In an earlier blog, our colleagues aptly stated that the 6G train has left the station and the long-anticipated journey has begun. Now we must make sure that the 6G train stays on its tracks and that every carriage and even the entire railway system is protected.
Within 3GPP, 15 active working groups shape different parts of the new 6G system. The Service and System Aspects Working Group 3 (SA3) is responsible for security and privacy, setting requirements, architecture, and protocols that protect mobile communication systems. For 6G, SA3 members took additional time to thoroughly assess the scope of the RAN and Architecture studies, ensuring a clear view could be formed of what must be done to ensure a robust 6G security posture.
Nokia has a long-standing track record in driving security standards, including in 3GPP, and is committed to networks that are secure-by-design and safeguard privacy and protect user identity. As such, Nokia is a leading contributor to SA3 and has chaired the group for the past four years. At the recent SA3 meeting in Gothenburg (Aug 25–29, 2025), 3GPP members prioritized security technologies essential for 6G day one. Ahead of this meeting, Nokia moderated the effort to build a common understanding among all members by distilling all members’ contributions into a document outlining 15 potential work tasks.
Nokia consistently underscored during the SA3 discussion the importance of secure-by-design principles across radio, network, and application layers. With 6G, the goal isn’t to reinvent everything from scratch, but to determine what can be carried over from 5G, what needs to be reinforced, and where new capabilities are essential.
Security isn’t about perfect protection. It’s about managing and reducing risks appropriately to keep the network and users safe in a complex and connected world. Instead of taking on the impossible task of eliminating all risks, the focus should be on understanding, prioritizing, and mitigating major risks effectively. Risk management helps to decide where to invest security efforts to get the best protection without overburdening resources.
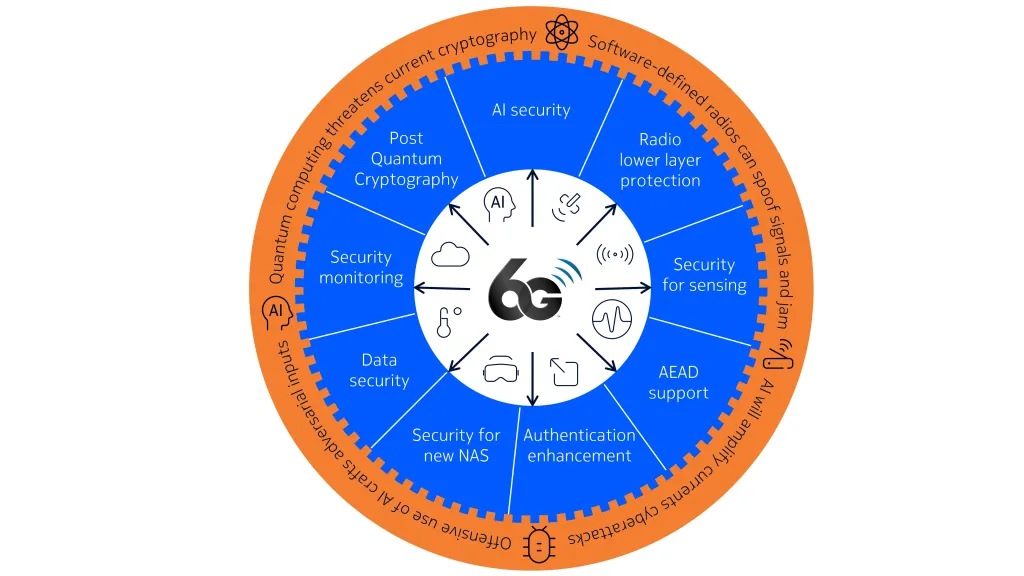
Based on this reasoning, Nokia considers the following list as the most important security study items for 6G, with the first three having potentially the greatest impact.
Post-Quantum Cryptography (PQC)
Future cryptographically relevant quantum computers (CRQCs) are anticipated to break classical cryptography, exposing stored sensitive data. To address this, Nokia has led Release 19 cryptographic inventory work, is contributing to IETF protocols and post-quantum migration planning. This establishes the foundation for evolving 3GPP systems toward quantum-resistant standards. In May, SA3 approved a follow-up Post-Quantum Cryptography (PQC) study to secure 6G from inception while enabling 5G migration to quantum-safe protection. With several governments setting PQC transition timelines, 3GPP specifications are expected to align with these targets, ensuring future-proof security across mobile networks.
AI security
As 6G is expected to leverage AI capabilities extensively, having a robust AI security framework in place is critical to prevent breaches, manipulation, and misuse. This framework preserves trust, regulatory compliance, and reliability amid evolving threats. In 6G, AI security includes safeguards, governance frameworks, and technical controls to protect AI agents, data, and automation processes from adversarial attacks while ensuring secure operations, lifecycle management, and user privacy. The debate in 3GPP is not about the importance of the topic, but rather about what should be standardized and what should be left to implementation. In 3GPP we are also confronted with three divergent AI regulation approaches: the U.S. Winning the AI Race: America’s AI Action Plan, China’s Artificial Intelligence Global Governance Action Plan, and the EU’s AI Act, which we must navigate in order to establish one single global 6G standard. The goal of this study is to build consensus among all stakeholders on this topic. As Nokia, we firmly believe in the value of standards also for AI security, as they are the best guarantee for interoperability and technological excellence.
Radio lower layer protection
While software-defined radios are primarily designed for flexible, legitimate radio experimentation and communication, their programmability and wide frequency range can be misused. They give attackers a highly versatile, low-cost tool to monitor, manipulate, or disrupt radio communications across all radio layers, including the lower layers.
Wireless generations up to and including 5G do not protect the radio layers below the PDCP layer. On top, UE Initial Messages are sensitive to identity and authentication attacks. And spoofing System Information Broadcast (SIB) messages opens up a range of threats on the devices.
In 6G, new radio spectrum and use cases are emerging, accompanied by enhanced radio layer functionalities to support expanded control and user plane features. Building on 5G, which added extra MAC Control Elements (MAC-CEs) for faster signaling, this trend is expected to continue in 6G. Since MAC-CEs carry privacy- and security-sensitive data, they require better protection.
Given these new threat vectors, it is prudent to secure the lower radio layers from the outset of 6G.
Data security
Data is a critical asset, not only for AI, but also for other 6G system capabilities such as system monitoring. As such, data security is essential to ensure confidentiality, integrity, and availability of critical data assets in different layers of the network. It embeds protections for data collection, storage, appropriate exposure, and user consent management, compliant to privacy regulations. With growing data sharing and third-party exposure, securing data across all layers preserves privacy, builds trust, and enables 6G networks to deliver enhanced reliable services.
Security for new NAS
New NAS (also known as Modular NAS) distributes and terminates multiple Non-Access Stratum (NAS) connections and related security across multiple nodes in the 6G Core Network. This contrasts with 5G NAS whereby only a single NAS connection exists and is terminated at one central point in the 5G Core Network (i.e. access and mobility management function, AMF). From a security perspective “New NAS” presents an opportunity to apply differentiated security across these distributed NAS connections. At the same time, careful attention must be paid to the growing number of nodes terminating NAS connections, particularly regarding security key distribution and the cipher suites employed by these terminating nodes.
AEAD support
Currently, NAS and Access Stratum (AS) security leverage existing cryptographic algorithms such as SNOW, ZUC and AES, to do encryption and integrity protection in separate steps. The Authenticated Encryption with Associated Data (AEAD) algorithms combine encryption and integrity protection in a single operation, offering benefits such as single-pass operation for both procedures. They also simplify system design by reducing the need of separate algorithms and keys for encryption and integrity protection, thus lowering complexity and error risk in the cryptographic process. As a result, these algorithms provide stronger protection against attacks, while lowering computational overhead and thus motivating to study AEAD support in 6G. Last week, we agreed on a dedicated AEAD 6G study.
Authentication enhancement
With technological advancements and lessons learned from past generations, enhancements in the authentication procedures (i.e. primary authentication, re-authentication, secondary authentication and so on) are necessary across different access and device types to support different use cases. These improvements may include the introduction of digital identities to better meet future security and flexibility requirements.
Security for sensing
Integrated Sensing and Communications (ISAC) technology merges radar-like sensing with wireless communication. This introduces several distinct security and privacy challenges. Unlike traditional networks, sensing systems need to process large volumes of raw data, probably outside the conventional base stations. Adequate transport security protection is necessary for this data to prevent any spoofing or manipulation up to the processing node. Invocation of the sensing capability needs to be restricted only to specific authenticated and authorized agents. The sensed data is highly sensitive, carrying both privacy and security implications. To address these risks, 3GPP SA3 is expected to work closely with RAN and architecture working groups in defining a holistic security framework for ISAC.
Security monitoring
Real-time, network-wide visibility of security events is now considered essential, surpassing node-level monitoring. For 6G, there is strong interest in dynamic monitoring to gain greater insights into system behavior enabling informed actions to be subsequently taken where need be, for example adjust access controls, bandwidth, and service quality based on real-time threats. By collecting, correlating and leveraging security data from both devices and networks, operators can enable more effective detection and real-time protection, ensuring stronger, adaptive defenses for future mobile systems.
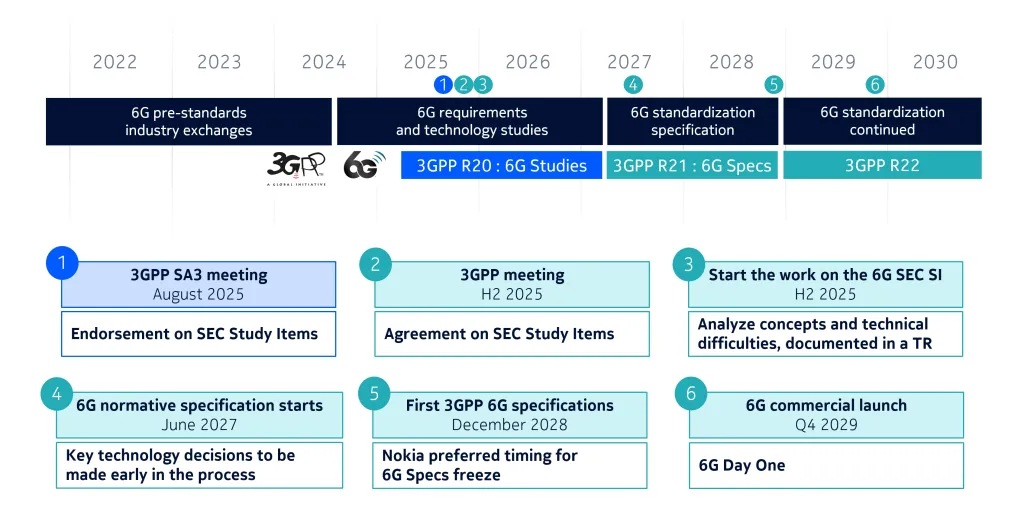
During this meeting, we only reached consensus on the 'endorsement of the 6G system security study with broad objectives' with formal approval expected later this year. We do not expect this slight delay to have a significant impact on the long run and will continue advocating for an early start to the detailed 6G security study.
With this timeline, we are on track to design the most cyber-resilient and secure network to date. Nokia aims to continue driving the work in SA3 with a secure-by-design mindset, focusing primarily on PQC, AI security, and enhanced radio lower layer protection as key priorities.







